How the new Spirion-Thales partnership enables sensitive-data-centric encryption
Thales Cloud Protection & Licensing
JUNE 29, 2022
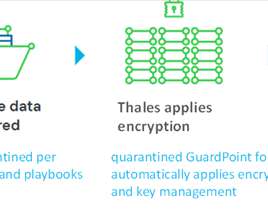
How the new Spirion-Thales partnership enables sensitive-data-centric encryption. Planning your enterprise security posture should work the same way. The security must be embedded with the data wherever it travels. Encryption achieves this goal by making the data readable only to those individuals with the proper access levels.















































Let's personalize your content