Researchers Quietly Cracked Zeppelin Ransomware Keys
Krebs on Security
NOVEMBER 17, 2022
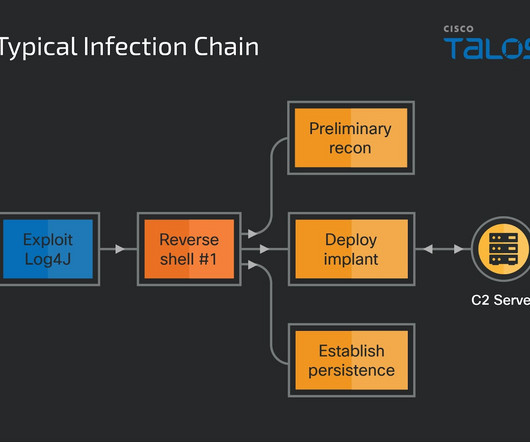
Peter is an IT manager for a technology manufacturer that got hit with a Russian ransomware strain called “ Zeppelin ” in May 2020. There are multiple examples of ransomware groups doing just that after security researchers crowed about finding vulnerabilities in their ransomware code. This is not an idle concern.















































Let's personalize your content