Access:7 flaws impact +150 device models from over 100 manufacturers
Security Affairs
MARCH 8, 2022
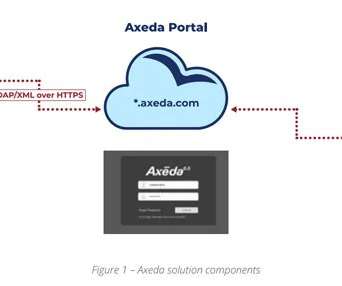
. “Access:7 could enable hackers to remotely execute malicious code, access sensitive data or alter configuration on medical and IoT devices running PTC’s Axeda remote code and management agent.”reads The platform allows remote access and management of connected devices to manufacturers through an agent is installed on devices.











































Let's personalize your content