ADVERSARIAL OCTOPUS – ATTACK DEMO FOR AI-DRIVEN FACIAL RECOGNITION ENGINE
Security Affairs
JUNE 22, 2021
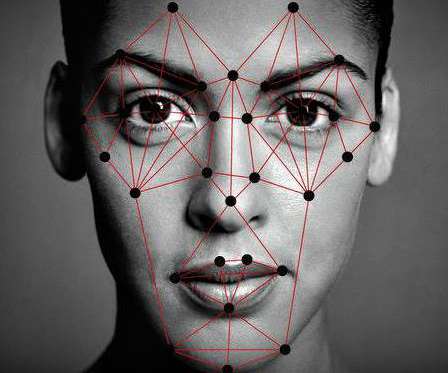
We aim to raise awareness and help enterprises and governments deal with the emerging problem of Adversarial Machine Learning. ATTACK DEMO. You can see a demo of the ‘Adversarial Octopus’ targeted attack below. Original post at: Face Recognition Attack Demo: Adversarial Octopus. ATTACK DETAILS.






































Let's personalize your content