A Threat to Passkeys? BrutePrint Attack Bypasses Fingerprint Authentication
eSecurity Planet
MAY 22, 2023
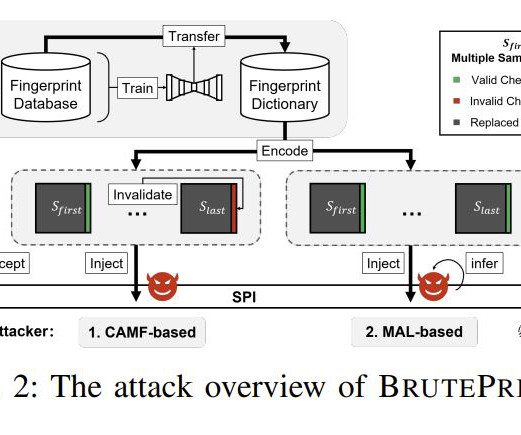
Security researchers recently published a paper detailing an attack they say can be used to bypass smartphone fingerprint authentication. “Instead of an implementation bug, CAMF and MAL leverage logical defects in the authentication framework,” the researchers wrote. And the attack is cheap to carry out.











































Let's personalize your content