Decoupling for Security
Schneier on Security
NOVEMBER 8, 2023
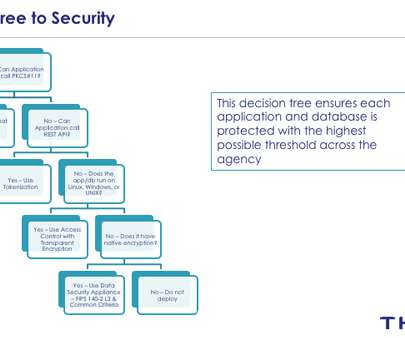
This is an excerpt from a longer paper. We can and should get the benefits of the cloud while taking security back into our own hands. The decoupling principle applies that idea to cloud services by making sure systems know as little as possible while doing their jobs. Here we outline a strategy for doing that.






































Let's personalize your content