European rulings on the use of Google Analytics and how it may affect your business
Data Protection Report
FEBRUARY 14, 2022
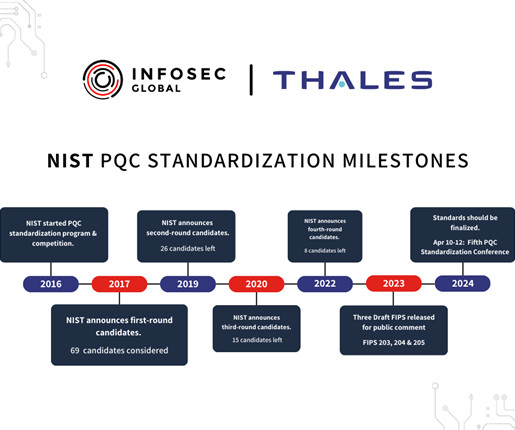
Recent decisions out of the EU will impact the use of Google Analytics and similar non-European analytics services when targeting EU individuals, with the potential to put many organizations at risk of receiving GDPR fines. At issue was the transfer of personal data from the EU to the US through the use of Google Analytics.
















































Let's personalize your content