US CISA Aims to Expand Automated Malware Analysis Support
Data Breach Today
APRIL 10, 2024
US Cyber Defense Agency Scales Next-Generation Malware Analysis Platform The U.S.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Data Breach Today
APRIL 10, 2024
US Cyber Defense Agency Scales Next-Generation Malware Analysis Platform The U.S.

Data Breach Today
APRIL 8, 2024
Environmental Protection Agency is investigating claims that a notorious government hacker leaked a trove of contact information from the agency's database of critical infrastructure contractors. A spokesperson said the agency conducted a "preliminary analysis" of the allegedly leaked data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
JANUARY 2, 2024
(This is a serious analysis, and the methodology looks sound.) Future research should aim towards a more comprehensive analysis to determine the potential influence of TikTok on popular public narratives.

Data Breach Today
MARCH 15, 2022
The ISMG Security Report features an analysis of the U.S. government's request for billions of dollars in tech aid to curb the global impact of the Kremlin's campaign in Ukraine. It also examines Biden's cryptocurrency executive order and why breached organizations often don't share full details.

IT Governance
MAY 18, 2023
The post IT Governance Podcast 19.5.23: A Capita special, featuring pension providers, Colchester City Council and Alan Calder’s analysis appeared first on IT Governance UK Blog. Plus, accusations of another Capita breach and Alan Calder on what all organisations can learn from the attack and Capita’s response.

Data Breach Today
JANUARY 29, 2019
Around the world, many CIOs at various levels of governments expect an increase in cybersecurity spending in 2019, according to new research from Gartner. Alia Mendonsa, co-author of the report, analyzes the results of a global survey.

Security Affairs
FEBRUARY 16, 2024
CISA revealed that threat actors breached an unnamed state government organization via an administrator account belonging to a former employee. The government experts conducted an incident response assessment of the state government organization after its documents were posted on the dark web.

Schneier on Security
JANUARY 19, 2023
A group of Swiss researchers have published an impressive security analysis of Threema. We provide an extensive cryptographic analysis of Threema, a Swiss-based encrypted messaging application with more than 10 million users and 7000 corporate customers.

Data Breach Today
NOVEMBER 8, 2019
The latest edition of the ISMG Security Report offers an analysis of how Twitter allegedly was used to spy on critics of the Saudi Arabian government. Also featured: A preview of the new NIST Privacy Framework and an update on business email compromise attacks.
Security Affairs
MARCH 28, 2024
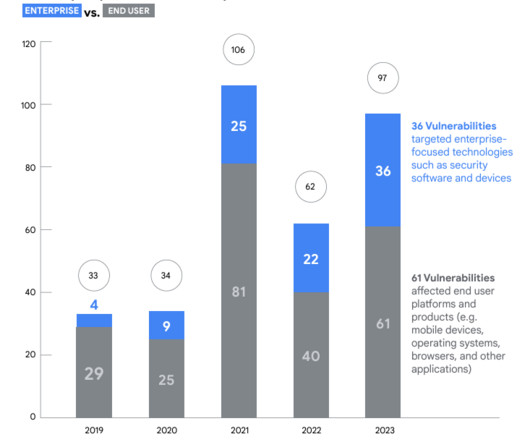
Google’s Threat Analysis Group (TAG) and Mandiant reported a surge in the number of actively exploited zero-day vulnerabilities in 2023. The Chinese government made the headlines because government-linked APT groups exploited 12 zero-day vulnerabilities in 2023, which marks a notable increase from seven in 2022.
Security Affairs
AUGUST 9, 2022
Cyber Security Specialist Zoziel Pinto Freire shows an example of malicious file analysis presented during his lecture on BSides-Vitória 2022. My objective with this series of articles is to show examples of malicious file analysis that I presented during my lecture on BSides-Vitória 2022. Static Analysis x Dynamic Analysis.

Data Breach Today
JANUARY 31, 2020
The latest edition of the ISMG Security Report discusses the ramifications of the U.K's decision to allow limited use of Huawei's equipment in 5G networks. Plus: Updates on Wawa's stolen card offered for sale and nascent security threats from social networks and drones.

Security Affairs
MARCH 19, 2024
The campaign seems active since at least early 2022 and focuses primarily on government organizations. The group often exploited access to government infrastructure to target other government entities. Analysis of the backdoors uploaded on VirusTotal revealed that threat actors utilized geopolitical topics as bait.

Data Breach Today
JANUARY 31, 2024
Information-Sharing Groups Call Reporting Requirements 'Too Costly, Overreaching' Multiple Information Sharing and Analysis Centers decried a proposed incident reporting measure for vendors selling to the U.S. federal government as being costly and ineffective.

Schneier on Security
AUGUST 31, 2023
A used government surveillance van is for sale in Chicago: So how was this van turned into a mobile spying center? Multiple Sony DVD-based video recorders store footage captured by cameras, audio recorders by high-end equipment brand Marantz capture sounds, and time and date generators sync gathered media up for accurate analysis.

The Last Watchdog
JUNE 23, 2023
June 22, 2023 — Dasera , the premier automated data security and governance platform for top-tier finance, healthcare, and technology enterprises, is thrilled to unveil “Ski Lift,” a complimentary platform exclusively designed for Snowflake users. Mountain View, Calif.
Security Affairs
NOVEMBER 16, 2023
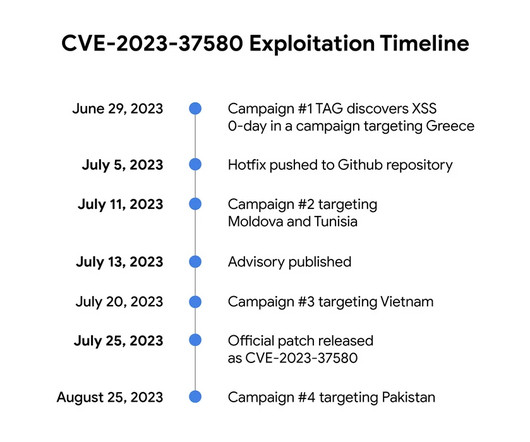
Google TAG revealed that threat actors exploited a Zimbra Collaboration Suite zero-day ( CVE-2023-37580 ) to steal emails from governments. The first campaign aimed at a government organization in Greece, threat actors sent emails containing exploit urls to their targets. ” continues the report. .”
Security Affairs
FEBRUARY 19, 2024
The nation-state actors are known to carry out cyber-espionage against targeting government, military, and national infrastructure entities in Europe and Central Asia since at least December 2020. The researchers recommend reading the detailed analysis of the recent TAG-70 campaign here.

Data Breach Today
MAY 14, 2019
Yet These Victims Are Less Likely to Pay Any Ransom, Recorded Future Finds Over the past two years, the number of ransomware attacks against state and local government agencies has increased. A new analysis by threat intelligence firm Recorded Future asks: Why the discrepancy?

Data Breach Today
OCTOBER 18, 2023
While RARLabs Patched Flaw, 'Many Users' Don't Appear to Have Updated the Software Nation-state hackers are targeting a vulnerability in WinRAR, a popular Windows utility for archiving files, warns Google’s Threat Analysis Group, which said it has seen "government-backed hacking groups" who hail from multiple countries, including China and Russia, (..)

erwin
SEPTEMBER 3, 2020
Why should you integrate data governance (DG) and enterprise architecture (EA)? Data governance provides time-sensitive, current-state architecture information with a high level of quality. Data governance provides time-sensitive, current-state architecture information with a high level of quality.
IBM Big Data Hub
SEPTEMBER 20, 2023
When implemented in a responsible way—where the technology is fully governed, privacy is protected and decision making is transparent and explainable—AI has the power to usher in a new era of government services. AI’s value is not limited to advances in industry and consumer products alone.

Data Breach Today
JULY 5, 2019
The latest edition of the ISMG Security Report analyzes the debate over whether the government should require technology firms to use weak encryption for messaging applications. Plus, D-Link's proposed settlement with the FTC and a CISO's update on medical device security.

Collibra
MAY 5, 2022
This requires every company to perform gap analysis to determine what is required and then update their systems, processes, workflows and data management strategy accordingly to ensure compliance. Their internal systems respect the governance and rules dictated by the standards, as well as the internal rules of the company.

Data Breach Today
DECEMBER 20, 2019
The latest edition of the ISMG Security Report discusses the recent ransomware attacks on the city of New Orleans as well as other units of local government and schools. Also featured: discussion on security issues for IoT and legacy medical devices.

IT Governance
SEPTEMBER 7, 2023
Transcript: Hello and welcome to the IT Governance podcast for Friday, 8 September 2023. The Cyber Essentials scheme is a government-backed framework supported by the National Cyber security Centre. IT Governance has been a certification body for the scheme since 2014, when it was launched.
Security Affairs
MARCH 7, 2023
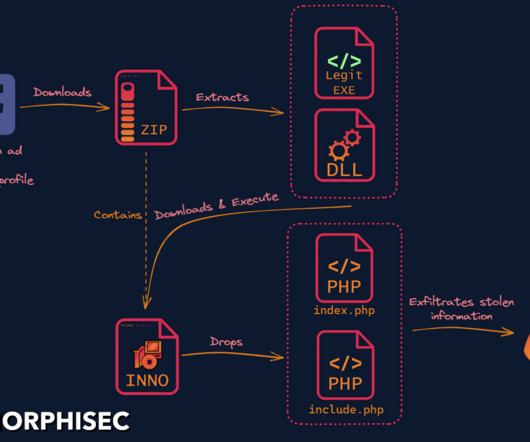
Researchers discovered a new info stealer dubbed SYS01 stealer targeting critical government infrastructure and manufacturing firms. ” reads the analysis published by Morphisec. to lure victims into downloading a malicious file. .” ” concludes Morphisec that also provides indicators of compromise (IoCs).

Security Affairs
AUGUST 26, 2021
Cybersecurity and Infrastructure Security Agency (CISA) released five malware analysis reports (MARs) related to samples found on compromised Pulse Secure devices. CISA published five malware analysis reports (MARs) related to samples found on compromised Pulse Secure devices. ” reads CISA’s advisory. ” reads the MAR.
Security Affairs
NOVEMBER 21, 2023
Experts warn of a surge in NetSupport RAT attacks against education, government, and business services sectors. The most impacted sectors are education, government, and business services. ” reads the analysis published by Carbon Black Managed Detection & Response team.

Collibra
JANUARY 9, 2024
In today’s world, data drives many of the decisions made by federal and state government agencies. High-quality data about vaccine supplies and population densities can lead to a successful distribution strategy, saving lives and strengthening public trust in the government’s response to the crisis.

IBM Big Data Hub
OCTOBER 4, 2022
Customers, employees and shareholders expect organizations to use AI responsibly, and government entities are demanding it. Failure to meet regulations can lead to government intervention in the form of regulatory audits or fines, damage to the organization’s reputation with shareholders and customers, and revenue loss.

OpenText Information Management
FEBRUARY 25, 2021
The effects of the SolarWinds attack will be felt for a long time, and will ripple far beyond the government alone. Even though investigations and analysis of the discovered hack remain ongoing, it has become clear that the scope is extensive, and the full impacts will likely prove to be devastating.

Security Affairs
MARCH 9, 2022
government. government. The campaign took place in February and Google Threat Analysis Group (TAG) team was not able to link it to the ongoing invasion of Ukraine. The campaign took place in February and Google Threat Analysis Group (TAG) team was not able to link it to the ongoing invasion of Ukraine. government.

erwin
SEPTEMBER 19, 2019
Data governance isn’t a one-off project with a defined endpoint. Data governance, today, comes back to the ability to understand critical enterprise data within a business context, track its physical existence and lineage, and maximize its value while ensuring quality and security. Passing the Data Governance Ball.

erwin
OCTOBER 8, 2020
And as you make this transition, you need to understand what data you have, know where it is located, and govern it along the way. As organizations look to migrate their data from legacy on-prem systems to cloud platforms, they want to do so quickly and precisely while ensuring the quality and overall governance of that data.
Security Affairs
SEPTEMBER 20, 2021
Security researchers uncovered a large phishing campaign targeting multiple government departments in APAC and EMEA countries. . Researchers from cybersecurity firm Cyjax uncovered a large phishing campaign targeting multiple government departments in APAC and EMEA countries. . ” reads the analysis published by the experts.

erwin
APRIL 2, 2021
Data Security Starts with Data Governance. Lack of a solid data governance foundation increases the risk of data-security incidents. Without data governance, organizations lack the ability to connect the dots across data governance, security and privacy – and to act accordingly. Who is authorized to use it and how?

Security Affairs
AUGUST 7, 2020
Google published its second Threat Analysis Group (TAG) report which reveals the company has taken down ten coordinated operations in Q2 2020. Google has published its second Threat Analysis Group (TAG) report , a bulletin that includes coordinated influence operation campaigns tracked in Q2 of 2020. response to COVID-19.
Security Affairs
MARCH 27, 2023
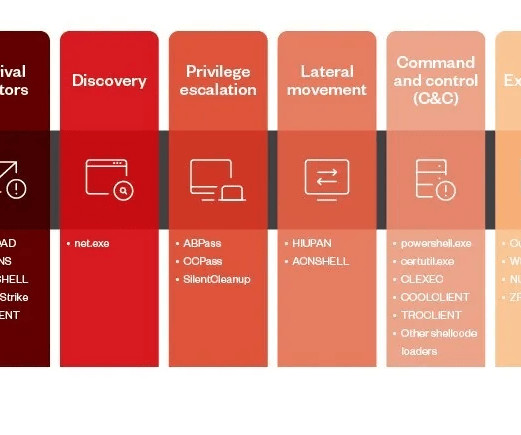
Earth Preta, also known as “RedDelta” or “Bronze President,” has been active since at least 2012, it targeted American and European entities such as government organizations, think tanks, NGOs , and even Catholic organizations at the Vatican.
Security Affairs
OCTOBER 13, 2023
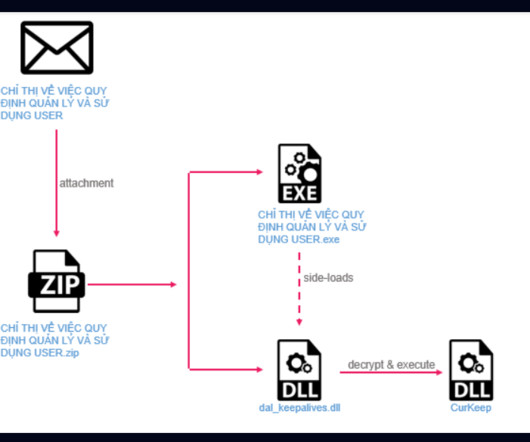
A cyberespionage campaign, tracked as Stayin’ Alive, targeted high-profile government and telecom entities in Asia. ” reads the analysis published by Checkpoint. The analysis of the C2 allowed the researchers to discover other loader variants used by the threat actor, such as CurLu, CurCore, and CurLog.

erwin
FEBRUARY 13, 2020
When an organization’s data governance and metadata management programs work in harmony, then everything is easier. Data governance is a complex but critical practice. Data Governance Attitudes Are Shifting. Data Governance Attitudes Are Shifting. Impact Analysis (48%). Why such a heavy lift? Data Mapping (53%).

erwin
MARCH 25, 2021
erwin recently hosted the second in its six-part webinar series on the practice of data governance and how to proactively deal with its complexities. Led by Frank Pörschmann of iDIGMA GmbH, an IT industry veteran and data governance strategist, the second webinar focused on “ The Value of Data Governance & How to Quantify It.”.

Security Affairs
JUNE 6, 2022
Following the attacks of the Killnet Collective, the group responsible for the attacks against major government resources and law enforcement, a new group has been identified called “Cyber Spetsnaz”. The post Exclusive: Pro-Russia group ‘Cyber Spetsnaz’ is attacking government agencies appeared first on Security Affairs.

erwin
JANUARY 30, 2020
I’m excited to share the results of our new study with Dataversity that examines how data governance attitudes and practices continue to evolve. Defining Data Governance: What Is Data Governance? . 1 reason to implement data governance. Most have only data governance operations.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content