Microsoft’s case study: Emotet took down an entire network in just 8 days
Security Affairs
APRIL 4, 2020
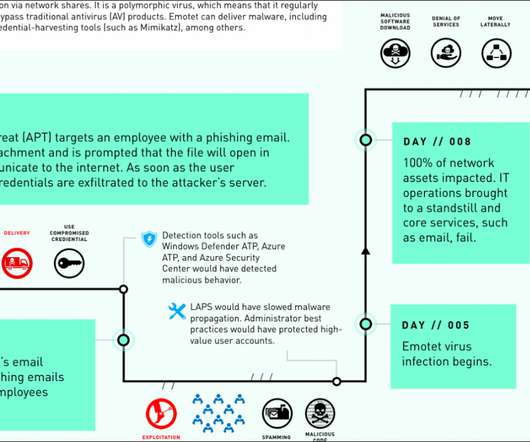
Microsoft shared details of the Emotet attack suffered by an organization named Fabrikam in the Microsoft’s Detection and Response Team (DART ) Case Report 002 , where Fabrikam is a fake name the IT giant gave the victim. “We are glad to share the DART Case Report 002: Full Operational Shutdown. Pierluigi Paganini.



































Let's personalize your content