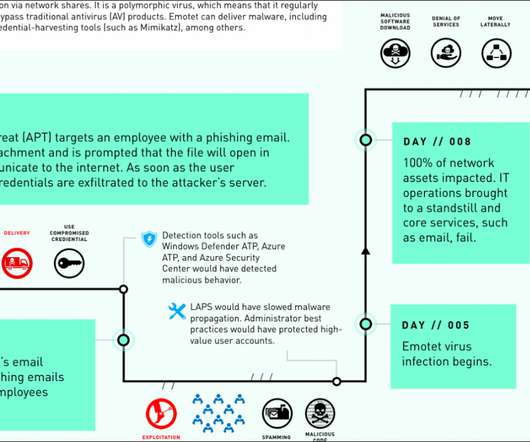
Microsoft’s case study: Emotet took down an entire network in just 8 days
Security Affairs
APRIL 4, 2020
‘We want to stop this hemorrhaging,’ an official would later say,” states DART case study report. The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.



































Let's personalize your content