Optiv CEO Kevin Lynch on Getting Value Via Unstructured Data
Data Breach Today
JANUARY 20, 2023
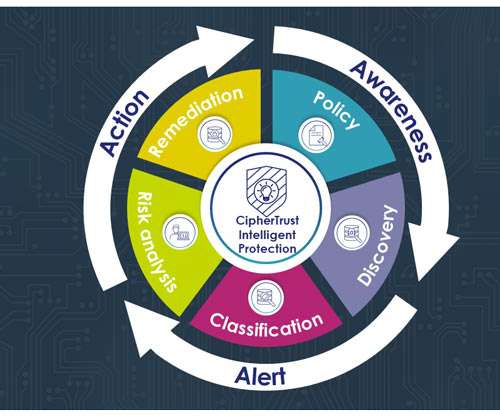
Why Clients Should Go Beyond Logs and Probe Transaction Data and System Interfaces Optiv has gone beyond examining log data and classic managed security services work to pursue threats across a broader swath of structured and unstructured data.














































Let's personalize your content