What VCs See Happening in Cybersecurity in 2023
eSecurity Planet
DECEMBER 7, 2022
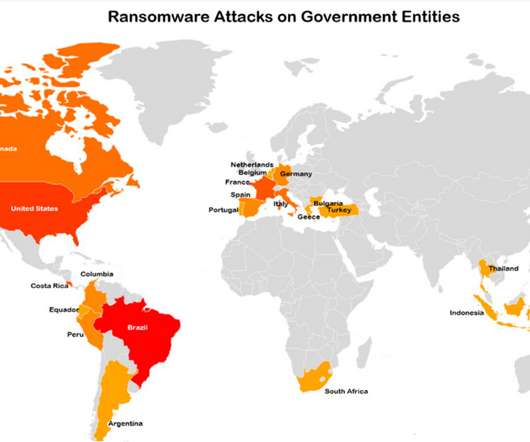
Despite all this, there is one tech category that has held up fairly well: Cybersecurity. Just look at a report from M&A advisory firm Houlihan Lokey , which found that private cybersecurity company funding grew by 9.4% There have been a number of impressive funding rounds this year for cybersecurity startups.
















































Let's personalize your content