GUEST ESSAY: The Top 5 online privacy and data security threats faced by the elderly
The Last Watchdog
JUNE 9, 2022
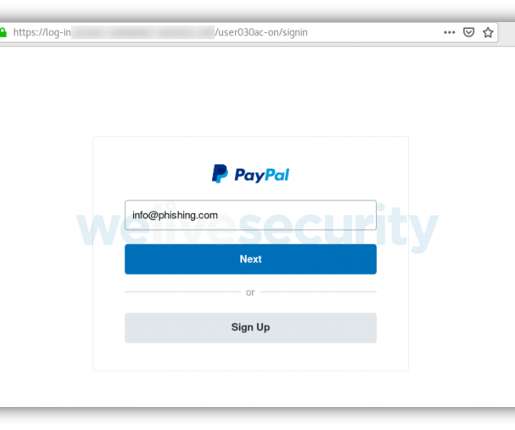
And, let’s be honest , the deceptive writing phishing assaults and other cyber threats today employ are skilled enough to fool even the most trained, internet-savvy experts. Ever present threats. A criminal exploiting someone’s medical or insurance details to make fraudulent claims is known as medical identity theft.

















































Let's personalize your content