Medibank Defends its Security Practices as its Ransomware Woes Worsen
IT Governance
NOVEMBER 17, 2022
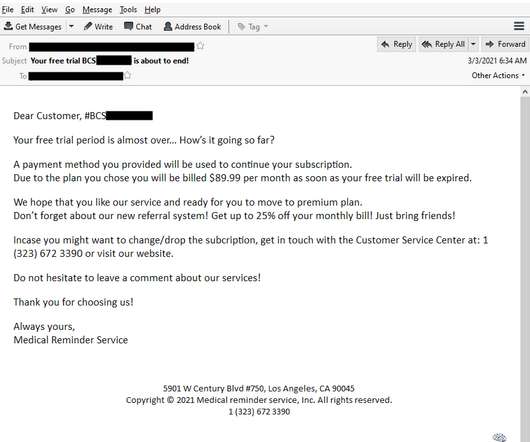
In most cases, basic personal information – such as their name, date of birth, email address, phone number and gender – was exposed. The first was damaging enough, containing patients’ names, addresses and birthdates. Things got worse for Medibank after a second database was leaked , containing a file named “abortions”.

































Let's personalize your content