macOS Backdoor RustDoor likely linked to Alphv/BlackCat ransomware operations
Security Affairs
FEBRUARY 10, 2024
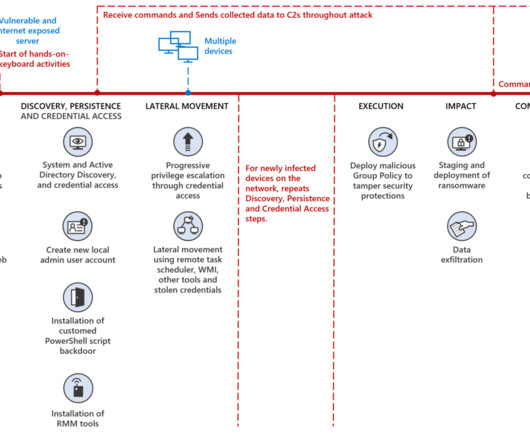
The researchers noticed that the backdoor contained a plist file named ‘test’. Some configurations also include specific instructions about what data to collect, such as the maximum size and maximum number of files, as well as lists of targeted extensions and directories, or directories to exclude” Bitdefender continues.

































Let's personalize your content