3 new steps in the data mining process to ensure trustworthy AI
IBM Big Data Hub
AUGUST 15, 2022
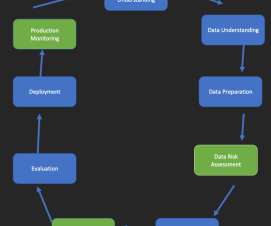
How does a data architecture impact your ability to build, scale and govern AI models? To be a responsible data scientist, there’s two key considerations when building a model pipeline: Bias: a model which makes predictions for people of different group (or race, gender ethnic group etc.) Data risk assessment.
















































Let's personalize your content