Hackers Are Now Exploiting Windows Event Logs
eSecurity Planet
MAY 10, 2022
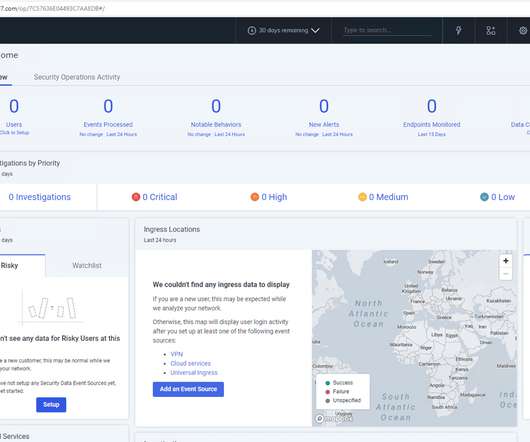
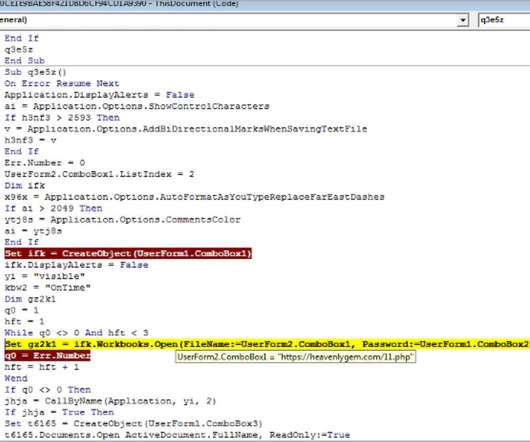
Hackers have found a way to infect Windows Event Logs with fileless malware , security researchers have found. During a “very targeted” campaign, hackers used Windows Event Logs to inject shellcode payloads and operate stealthily. If it does not find one, the encrypted shell code is written in 8KB chunks in the event logs.










































Let's personalize your content