Belgian Council of State Considers Encryption a Sufficient Measure for U.S. Data Transfers
Hunton Privacy
SEPTEMBER 9, 2021
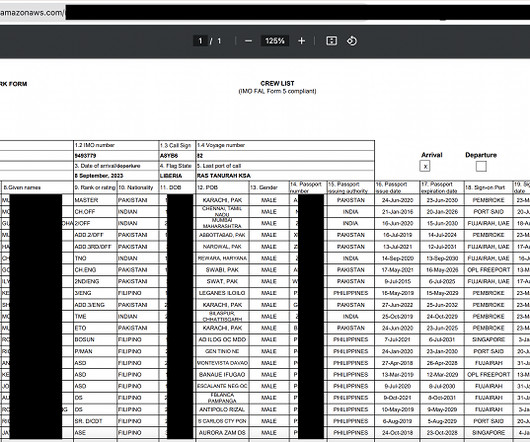
company using Amazon Web Services (“AWS”). The decision was made in the context of a tender granted by the Flemish Authorities to a company that used AWS cloud services. cloud services in and of itself does not violate the GDPR.
















































Let's personalize your content