Fake Emergency Search Warrants Draw Scrutiny from Capitol Hill
Krebs on Security
MARCH 31, 2022
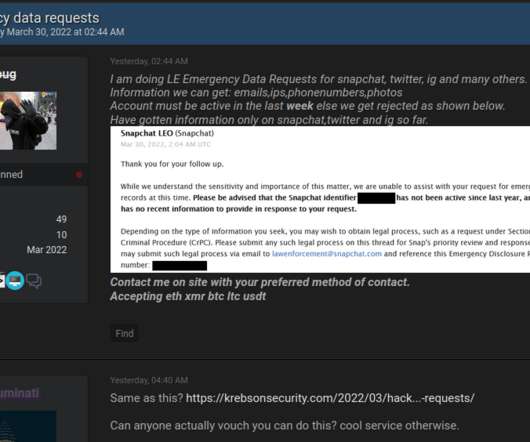
One example can be found on Telegram, wherein a member who favors the handle “ Bug ” has for the past month been selling access to various police and government email accounts. 30, Bug posted a sales thread to the cybercrime forum Breached[.]co Bug posted this sales thread on Wednesday.













































Let's personalize your content