Chinese Hacking Contractor iSoon Leaks Internal Documents
Data Breach Today
FEBRUARY 20, 2024
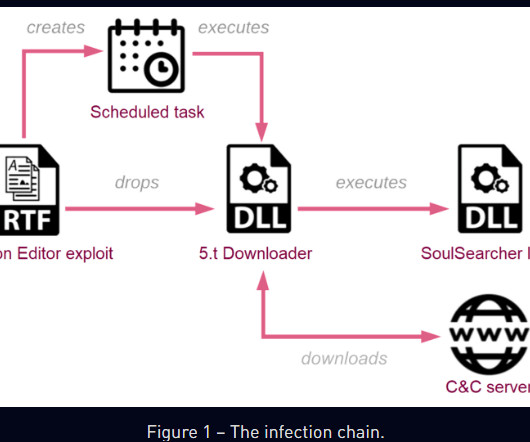
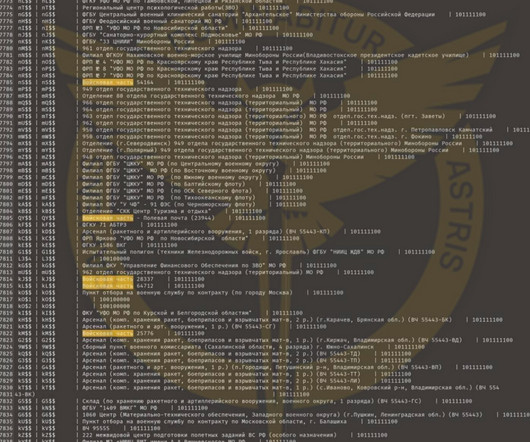
Company Mainly Hacked for the Ministry of Public Security An apparent leak of internal documents from a Chinese hacking contractor paints a picture of a disaffected, poorly paid workforce that nonetheless penetrated multiple regional governments and possibly NATO.





































Let's personalize your content