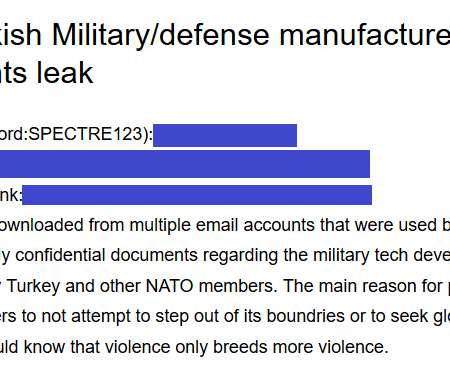
Researchers found alleged sensitive documents of NATO and Turkey
Security Affairs
OCTOBER 12, 2020
Security experts from Cyble found alleged sensitive documents of NATO and Turkey, is it a case of cyber hacktivism or cyber espionage? “These events ensue an unsatisfying narrative – Is it really hacktivism or cyber espionage?” ” reads the post published by Cyble. Pierluigi Paganini. SecurityAffairs – hacking, NATO).












































Let's personalize your content