Weekly Update 354
Troy Hunt
JULY 2, 2023
Book a demo. 😊 References Sponsored by Kolide. Kolide can get your cross-platform fleet to 100% compliance. It's Zero Trust for Okta. Want to see for yourself?
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Troy Hunt
JULY 2, 2023
Book a demo. 😊 References Sponsored by Kolide. Kolide can get your cross-platform fleet to 100% compliance. It's Zero Trust for Okta. Want to see for yourself?

Troy Hunt
JULY 28, 2023
Watch the demo today! BreachForums, was itself, breached (definitely legit too, given the presence of a "lurker" account I created there) It's Device Trust for Okta. The BookCrossing breach went into HIBP (plain text passwords FTW!) The BookCrossing breach went into HIBP (plain text passwords FTW!)
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
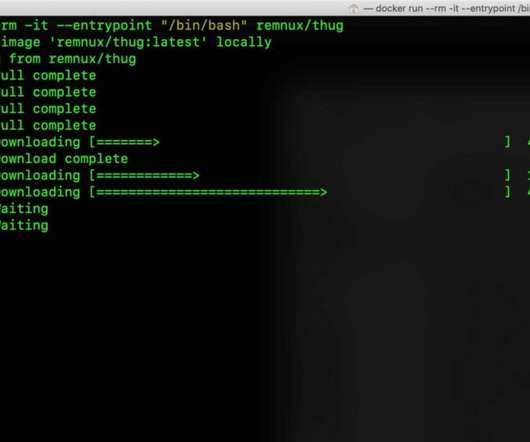
eSecurity Planet
NOVEMBER 7, 2022
We’ll examine the pros and cons, but REMnux is definitely a great asset for those who want to focus on their work and skip the “installation hell.”. Python, PowerShell , Java) Analyzing memory for code injections and other malicious activities Examining suspicious documents (such as PDFs, Microsoft Office, emails). Why Use REMnux?

Collibra
MARCH 28, 2024
An integrated platform allows data engineers to focus on their own tasks while non-technical users are empowered to create business definitions, policies and regulatory standards. Reach out to us here for a full demo and to learn more. In addition, a solution that combines governance with AI models (i.e.,

erwin
AUGUST 6, 2020
Data Literacy Definition. It also provides a business glossary for the collaborative definition of enterprise data in business terms. Click here for a free demo of erwin Data Intelligence. So, what is data literacy? What Is Data Literacy? erwin DL provides self-service, role-based, contextual data views.
erwin
APRIL 15, 2020
Does the definition (description, classification, allowable range of values, etc.) of incoming, individual data elements match our internal definitions of those data elements? We’d be happy to provide a demo of how to use erwin DI for data distancing. What formulas were used?

erwin
JUNE 26, 2020
It defines the functionality of the data captured, definition of the data, definition of the elements, and definition of how the data is used within the business. Data asset need to be properly scanned, documented, tagged and annotated with their definitions, ownership, lineage and usage. appeared first on erwin, Inc.

erwin
MARCH 12, 2020
But isn’t the definition of insanity doing the same thing over and over, expecting but never realizing different results? Click here to request a free demo of erwin DI. Our clients often understand that incredible DevOps improvements are possible, but they fear the “work” it will take to get there.

erwin
DECEMBER 3, 2020
This metadata is ingested into the data catalog, definitions are added within a business glossary, and the searchable repository enables users to understand how data is used and stored. You also can request a free demo of erwin DI here. Click here to download a copy of the Gartner Magic Quadrant Report.

Collibra
JUNE 17, 2021
Attendees had the opportunity to ask our experts questions and see demos of Collibra Data Governance, Collibra Data Privacy, Collibra Data Quality, and Collibra Data Catalog. Insights Exchange: A conversation with Neil deGrasse Tyson: This session was definitely a show stopper and an out-of-this-world experience!

erwin
JUNE 22, 2020
Request a free demo of erwin DI. This style of data governance most often presents us with eight one-hour opportunities per day (40 one-hour opportunities per week) to meet. And ultimately, we’ll take up less of our colleagues’ precious time.
erwin
FEBRUARY 28, 2024
And truth must be told, the demo of erwin Data Intelligence left us impressed. From the first demo we fell in love with the unique way they approach data governance, with a holistic view on business terms, with governance flexibility really baked into the system, with fast responses to all our questions and with the right values.

Everteam
JANUARY 9, 2019
With it, you can: Create comprehensive policy definitions. Everteam.policy allows you to assign intermediate milestones to your policy definitions related to how a piece of content is stored, indexed or the metadata applied to it. In everteam.policy, every policy has a unique code, name, and description.

Collibra
MARCH 24, 2022
That uniqueness is good (and normal), but it also means that a specific definition of data enablement needs to be created for every individual organization. . Once you’ve determined what your unique definition of data enablement is, you’re ready to tackle your data-enablement journey. Step 7: Meet the business in the middle .

IBM Big Data Hub
JANUARY 8, 2024
This means they can be understood by people, are supported by code generation tools and are consistent with API definitions. This includes lifecycle management, versioning and definition of policy-based controls. Event Endpoint Management produces valid AsyncAPI documents based on event schemas or sample messages.

Security Affairs
APRIL 3, 2020
Its contributors and developers confirmed that it will be no longer maintained and it will be definitively removed from the WordPress repository. 2020 – A serious flaw in the ThemeGrill Demo Importer WordPress theme plugin with over 200,000 active installs can be exploited to wipe sites and gain admin access to the site.

Data Protection Report
MARCH 21, 2024
name, mobile number, IP address, device ID) meets the definition of IIHI. Click here to request a demo. In this example, the transmission of information to a tracking technology vendor as a result of using such app would be disclosure of PHI because the individual’s use of the app is related to an individual’s health condition (i.e.,

Collibra
NOVEMBER 20, 2020
You’ve evaluated and demoed countless technologies and you think you’re ready to select a solution. Also include identification of stakeholders, definition/approval and issue management processes. Detailed process definition and technology education should be a roadmap step. You’ve read analyst reports and whitepapers.
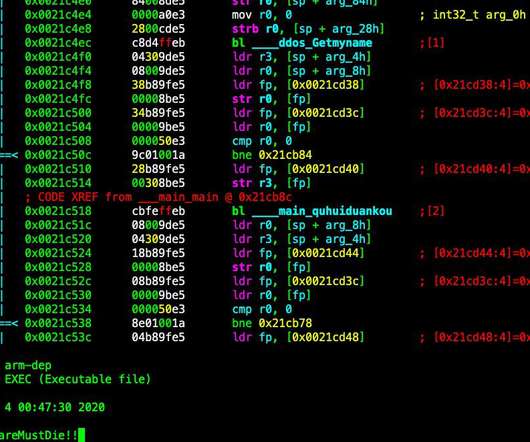
Security Affairs
MAY 5, 2020
“In late April we identified a new botnet campaign with definitive Chinese origins,targeting servers and IoT devices via SSH brute forcing. The Kaiji malware is different from other IoT ELF malware, it is written from scratch in the Go programming language, and its detection rate at the time of discovery was only 1.

IBM Big Data Hub
AUGUST 2, 2023
Providing open access to observability data is crucial as IT systems evolve and job definitions expand. If you want to enhance your observability practices with full-stack visibility and the ability to monitor your cloud dependencies in real-time, we invite you to request a demo.

CILIP
FEBRUARY 23, 2021
demo th { border:1px solid #C0C0C0; padding:5px; background:#F0F0F0; }.demo demo td { border:1px solid #C0C0C0; padding:5px; }. We would definitely recommend you add Membership , Membership notifications and Member Services? TITLE.demo { border:1px solid #C0C0C0; border-collapse:collapse; padding:5px; }.demo

AIIM
MAY 13, 2019
As a project sponsor or agile project manager, you should definitely be on the lookout for this person, because if you can find them and secure them for your team, you will have given yourself a much-needed advantage in ensuring you ship a quality product. The Connected, Inspired, Hands-on Project Sponsor – Leading the Digital Charge.

Info Source
MARCH 5, 2018
To learn more about the Healthcare Workflows and see a demo, visit booth #1143 at HIMSS March 5-9 in Las Vegas. With the Outpatient Document Management Workflow, organizations can: Reduce time spent reconciling patient documentation and increase time spent with patients, Increase billing accuracy and timeliness, and.

IBM Big Data Hub
JULY 12, 2023
The tipping point came when a significant payroll model took six people half a day to resolve without a definitive answer, leading to a loss of confidence in the Excel model. Request a live demo The post GKN Aerospace — Journey to integrated business planning appeared first on IBM Blog.

Security Affairs
NOVEMBER 3, 2019
Instead, a hacker group has been using a demo BlueKeep exploit released by the Metasploit team back in September to hack into unpatched Windows systems and install a cryptocurrency miner. Due to only smaller size kernel dumps being enabled, it is difficult to arrive at a definite root cause.”

Collibra
NOVEMBER 11, 2019
Be flexible: If the business is struggling with a process, a definition doesn’t make sense, or another issue arises, engage and be willing to evolve. Meet the business in the middle: Develop assets in “plain English,” conduct demos, create metrics, and encourage self-service.

Collibra
NOVEMBER 11, 2019
Be flexible: If the business is struggling with a process, a definition doesn’t make sense, or another issue arises, engage and be willing to evolve. Meet the business in the middle: Develop assets in “plain English,” conduct demos, create metrics, and encourage self-service.

eSecurity Planet
MAY 19, 2023
Here we’ll take an in-depth look at five of the top application security tools, followed by features buyers should look for and an examination of different approaches to application and code security. It offers a wide range of security testing capabilities, including code scanning, vulnerability assessment , and penetration testing.

Everteam
JUNE 5, 2019
As part of the rule definition process, you either select existing criteria or create a new query that will find all the documents you want to apply the rule to. Request a demo and we’ll show you. For example, you want all contracts to be classified as type: Contracts. Interested in seeing how it works?

ForAllSecure
JULY 21, 2020
ADAM: I remember when I first started out, I definitely had the most experience with websites. Things like cryptography, assembly, reverse engineering and binary exploitation I've never seen before and it was definitely a lot harder. So that was definitely the hardest part about that. Request Demo Learn More.

erwin
JANUARY 11, 2019
Its hallmark is a consistent approach to data delivery (business glossaries connect physical metadata to specific business terms and definitions) and metadata management (via data mappings). If you want more control over and more value from all your data, join us for a demo of erwin MM.

OneHub
JULY 12, 2019
The conception of cloud services can be traced back to the 1950s, so it can be said that the cloud has some definite staying power. To learn more about cloud storage and what it can do for your business, reach out to Onehub for a complimentary demo. The post What Is the Best Cloud Storage?

IBM Big Data Hub
JULY 26, 2023
In this blog post, we will delve into the concept of zero-based budgeting, exploring its definition, advantages, disadvantages, implementation steps, and tools needed. Request a live demo The post What is zero-based budgeting? Learn more about IBM Planning Analytics What is Zero-Based Budgeting? appeared first on IBM Blog.

Everteam
FEBRUARY 6, 2019
Let’s get the Garter definition out of the way (Gartner analyst Doug Laney first defined the term Infonomics in the 1990s): “Infonomics is the emerging discipline of managing and accounting for information with the same or similar rigor and formality as other traditional assets (e.g., Learn how we can help you or contact us to set up a demo.

ForAllSecure
APRIL 4, 2023
There's definitely some tricky things in the cloud. And so you know, this is definitely one of those challenges people are facing and you know, one of the groups that we track at the moment for hacking group, they compromise. I've seen over my last 16 odd years in cybersecurity. CAMPBELL: The cloud is a real enabler.

OneHub
OCTOBER 7, 2021
During your free trial (which should definitely be on your list of “must haves”), pay attention to how well you can intuitively use different features. Screenshots and demo videos are great, but they don’t compare to working directly with the software. Is it immediately obvious how to upload a file? Free trial.

ForAllSecure
AUGUST 16, 2019
It would definitely make sense—makes more sense there. Brumley: Yeah, working with the government is definitely, it’s a chore until you get into the groove and you realize a lot of the, what you perceive are barriers, are actually just regulations put up to protect taxpayers from complete abuse. Ashley: Mm-hmm.

ForAllSecure
MAY 26, 2020
This definition is consistent with the IEEE 754 representation of floating point numbers, one variant of which prescribes to encode it in 80 bits of data as done by Intel. You can learn more about Mayhem by requesting a demo at the following link. A long double is represented using 12 bytes of padding and 8 bytes of actual data.

ForAllSecure
MAY 26, 2020
This definition is consistent with the IEEE 754 representation of floating point numbers, one variant of which prescribes to encode it in 80 bits of data as done by Intel. You can learn more about Mayhem by requesting a demo at the following link. A long double is represented using 12 bytes of padding and 8 bytes of actual data.

ForAllSecure
MAY 26, 2020
This definition is consistent with the IEEE 754 representation of floating point numbers, one variant of which prescribes to encode it in 80 bits of data as done by Intel. You can learn more about Mayhem by requesting a demo at the following link. A long double is represented using 12 bytes of padding and 8 bytes of actual data.

ForAllSecure
MARCH 25, 2020
My initial hunch was that opkg would download the package, unpack it to a temporary directory, and only then verify the SHA256 hash before definitively installing it to the system. Learn More Request Demo. After all, the package shouldn’t be processed if the SHA256 hash was incorrect.

ForAllSecure
AUGUST 16, 2019
It would definitely make sense—makes more sense there. Brumley: Yeah, working with the government is definitely, it’s a chore until you get into the groove and you realize a lot of the, what you perceive are barriers, are actually just regulations put up to protect taxpayers from complete abuse. Ashley: Mm-hmm.

ForAllSecure
AUGUST 16, 2019
It would definitely make sense—makes more sense there. Brumley: Yeah, working with the government is definitely, it’s a chore until you get into the groove and you realize a lot of the, what you perceive are barriers, are actually just regulations put up to protect taxpayers from complete abuse. Ashley: Mm-hmm.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content