How to Advocate for Data Privacy and Users' Rights
WIRED Threat Level
SEPTEMBER 28, 2022
Want to speak up against Big Tech, unjust data collection, and surveillance? Here's how to be an activist in your community and beyond.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

WIRED Threat Level
SEPTEMBER 28, 2022
Want to speak up against Big Tech, unjust data collection, and surveillance? Here's how to be an activist in your community and beyond.

The Last Watchdog
OCTOBER 23, 2023
Cisco’s $28 billion acquisition of Splunk comes at an inflection point of security teams beginning to adopt to working with modern, cloud-native data lakes. Related: Dasera launches new Snowflake platform For years, Splunk has been the workhorse SIEM for many enterprise Security Operation Centers (SOCs).
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IBM Big Data Hub
FEBRUARY 23, 2024
The GDPR applies to any organization that processes the personal data of European residents, regardless of where that organization is based. Finally, the GDPR applies to the processing of personal data for virtually any reason: commercial, academic, governmental, and otherwise. Consents cannot be bundled, either.

eDiscovery Daily
DECEMBER 1, 2021
When handling these confidential documents, it is important to keep these documents safe and secure. . As a vital part of the Electronic Discovery Reference Model (EDRM) , any data collected is done so with the intent to capture it exactly as intended or as it was actively being used. civil case collecting 130 GBs of data. .

Jamf
OCTOBER 17, 2023
Understanding the security needs of an organization is only one component of maintaining a strong security posture. Knowing the risks that are unique to your organization and assessing them accurately are critical to the overall security posture as well.

AIIM
MARCH 29, 2022
Data architecture is probably the first to rank. Scalability will be tested to the maximum due to the extreme data collection and data processing requirements coming from metaverse scenarios. Integration and data consumption will redefine their order of magnitude, and AI will be the de facto standard.
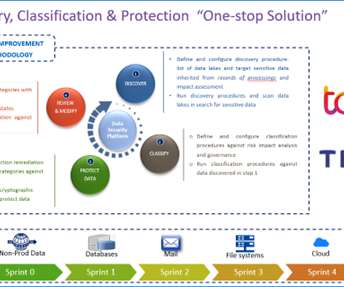
Thales Cloud Protection & Licensing
MAY 31, 2022
How to manage this complexity? To that effect, TCS, Global leader in cyber security services, and Thales recently announced a partnership offering a one-stop solution for data privacy that organisations leverage to manage this complexity and help reach compliance. The accountability of data controllers cannot be transferred.

Hunton Privacy
FEBRUARY 2, 2022
On January 28, 2022, in celebration of Data Privacy Day, the Colorado Attorney General’s Office issued prepared remarks from Colorado Attorney General Phil Weiser and published guidance on data security best practices. Regularly reviewing and updating security policies.

Thales Cloud Protection & Licensing
AUGUST 15, 2019
For example, data collected by an entity may not be associated with an individual but could identify a household. The CCPA applies to for-profit entities that both collect and process the PI Information of California residents and do business in the State of California, without a physical presence in California being a requirement.

IBM Big Data Hub
SEPTEMBER 6, 2023
AI marketing is the process of using AI capabilities like data collection, data-driven analysis, natural language processing (NLP) and machine learning (ML) to deliver customer insights and automate critical marketing decisions. What is AI marketing?
WIRED Threat Level
JUNE 1, 2022
Voice recognition—and data collection—have boomed in recent years. Researchers are figuring out how to protect your privacy.
WIRED Threat Level
JUNE 1, 2022
Voice recognition—and data collection—have boomed in recent years. Researchers are figuring out how to protect your privacy.

The Last Watchdog
APRIL 9, 2020
Data collected by IoT devices will increasingly get ingested into cloud-centric networks where it will get crunched by virtual servers. The many privacy and security issues raised by IoT, however, are another story. The addressing of IoT privacy and security concerns lags far, far behind.

eSecurity Planet
APRIL 8, 2021
Researchers now believe that the rapid adoption of these skills could have implications for information security as they could open Alexa users up to phishing or invasive data collection. Some examples include Alexa Guard for home security, Easy Meal Ideas for recipes and Spotify for music. What is an Amazon Alexa Skill?

Troy Hunt
NOVEMBER 25, 2020
Now for the big challenge - security. The "s" in IoT is for Security Ok, so the joke is a stupid oldie, but a hard truth lies within it: there have been some shocking instances of security lapses in IoT devices. But there are also some quick wins, especially in the realm of "using your common sense". Let's dive into it.

Krebs on Security
DECEMBER 20, 2022
In 2017, Equifax disclosed a massive, extended data breach that led to the theft of Social Security Numbers, dates of birth, addresses and other personal information on nearly 150 million people. Americans currently have no legal right to opt out of this data collection and trade. They received a check for $6.97.

erwin
JUNE 11, 2020
Blockchain enables more secure and complex transaction record-keeping for businesses. More businesses employing data intelligence will be incorporating blockchain to support its processes. Data quality management. Overseeing the data collection and processing and implementing governance of these is important.

eDiscovery Daily
NOVEMBER 10, 2021
Another consequence brought about by the lockdowns was the disruption of electronic discovery data collectio n. New strategies had to be developed around data collection as document review service providers had to order hard drives, copy relevant ESI onto the hard drives, and then deliver them to the client. . Cost reductions.

The Last Watchdog
JUNE 13, 2022
The top drivers of the continued growth of cybersecurity are: the growing need to protect the API supply chain, the inadequacy of existing identity management systems, and the unfulfilled promise of data-driven AI-powered cybersecurity systems. Securing APIs. Every week, we see a new pitch for an API supply chain security startup.

The Last Watchdog
SEPTEMBER 11, 2019
Security orchestration, automation and response, or SOAR, is a fledgling security technology stack that first entered the cybersecurity lexicon about six years ago. Saurabh told me he developed a passion for helping organizations improve the efficiencies of their security operations. billion, and later co-founded SumoLogic.

Security Affairs
OCTOBER 17, 2023
Authentication data collected by POEMGATE can be used for lateral movement and other malicious activities on the compromised networks. At the final stage of an attack, the attackers were able to interfere with network equipment, as well as data storage systems.

Data Matters
SEPTEMBER 28, 2021
This summer, the Federal Trade Commission (“FTC”) hosted its sixth annual PrivacyCon , an event focused on the latest research and trends related to consumer privacy and data security. The discussion highlighted the benefits of advertisement explanations that make clear to a user how and why they are targeted.

The Last Watchdog
DECEMBER 7, 2021
A digital twin is a virtual duplicate of a physical entity or a process — created by extrapolating data collected from live settings. As data collection and computer modeling have advanced apace, so have the use-cases for digital twin technology. Alexander. I’ll keep watch and keep reporting.

Privacy and Cybersecurity Law
FEBRUARY 8, 2022
On the same day, the Colorado AG released a data security best practices guide, outlining key steps organizations can take now to ensure their security practices align with Colorado law. Below we detail these developments, and provide two takeaways for organizations planning for CPA compliance in 2023. Key Takeaways.
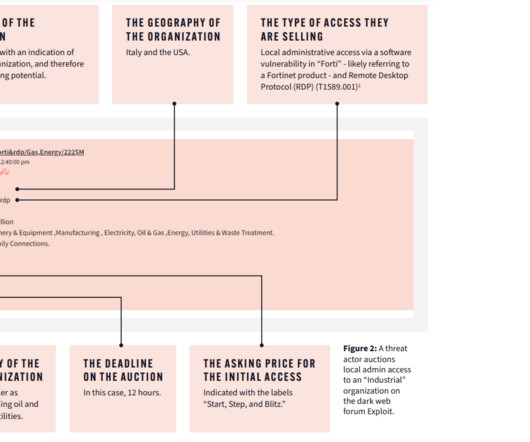
Security Affairs
MAY 17, 2023
The threat actors offered detailed instructions on how to exploit known vulnerabilities in Internet-facing ICS systems. Dark web intelligence is a fantastic resource for informing an organization’s security posture, helping the security team spot early indicators of attack and feeding their threat models. We are in the final!

IT Governance
NOVEMBER 17, 2020
Deliberate or accidental action (or inaction) by the school or one of the processors : an example would be sending old PCs, laptops or filing cabinets to be destroyed without first removing the data held on them. Sending personal data to the wrong person : this includes any message sent by email, post or fax. Identity theft or fraud.

OpenText Information Management
FEBRUARY 17, 2021
From litigation support personnel to the lawyers themselves, organizations face a common challenge: how to streamline processes and procedures to simplify and thoroughly respond to on-going litigation requests. This raises many questions: How do we streamline processes and procedures cost-effectively?
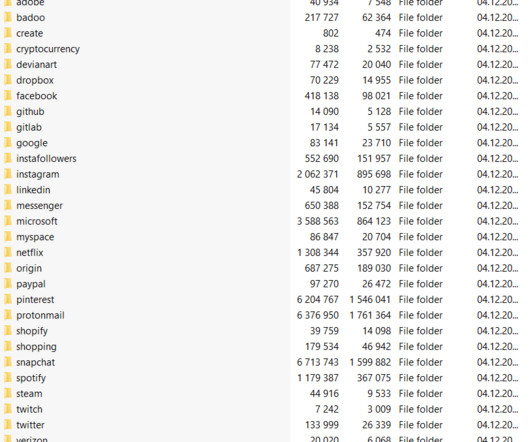
Security Affairs
APRIL 6, 2023
The creators of phishing bots and kits can get access to data that is gathered with their tools. “To attract larger audiences, scam operators advertise their services, promising to teach others how to phish for serious cash.” User personal data for sale. The cyber security firm reported that it has prevented 7.1

The Last Watchdog
JANUARY 23, 2024
“Knowing how to safeguard your personal information has never been more important than it is today. “As innovation continues to outpace regulation, individuals and businesses alike need to make concerted efforts to educate themselves and take a proactive role in preserving the privacy of sensitive data.

CGI
OCTOBER 24, 2017
How to compete in the cybersecurity talent tug of war. Across business and technology media alike, I’ve seen frequent coverage of the hundreds of thousands of cybersecurity and IT security job openings that are not getting filled. 1 (ISC)² Global Information Security Workforce Study (GISWS). harini.kottees…. million jobs.

Schneier on Security
MARCH 2, 2020
Recently announced Off-Facebook feature comes with similar issues, giving little insight into how advertisers collect your personal data and how to prevent such data collection.

The Last Watchdog
JUNE 2, 2021
The amount of data in the world topped an astounding 59 zetabytes in 2020, much of it pooling in data lakes. We’ve barely scratched the surface of applying artificial intelligence and advanced data analytics to the raw data collecting in these gargantuan cloud-storage structures erected by Amazon, Microsoft and Google.

Dark Reading
MAY 22, 2018
There are a lot of moving pieces involved with data collection, retention, and processing in the EU's new General Data Protection Regulation. Here's how to break down responsibilities between your security team and service providers.

IBM Big Data Hub
APRIL 24, 2024
These access controls reduce the chances that the data is used for unauthorized or illegal purposes. Learn how organizations can use IBM Guardium® Data Protection software to monitor data wherever it is and enforce security policies in near real time. Retention policies should also be limited.

Hunton Privacy
NOVEMBER 1, 2022
Businesses are required to document and maintain records of all consumer data rights requests, in a readable format, for at least twenty-four (24) months. Businesses are required to document and maintain records of all consumer data rights requests, in a readable format, for at least twenty-four (24) months. Authentication (Rule 4.08).

Security Affairs
OCTOBER 27, 2023
Then, the derived insights let you monitor market trends, customer behavior, competitor pricing, and other key data collected via market research. Successful extraction of public data from the internet can be a tricky process, especially when visited websites use protection algorithms. appeared first on Security Affairs.

IT Governance
NOVEMBER 14, 2018
Responsibilities of the data controller. A data controller takes top-level responsibility for data collection. If you have the authority to determine that information needs to be collected, you are a data controller. Responsibilities of the data processor.
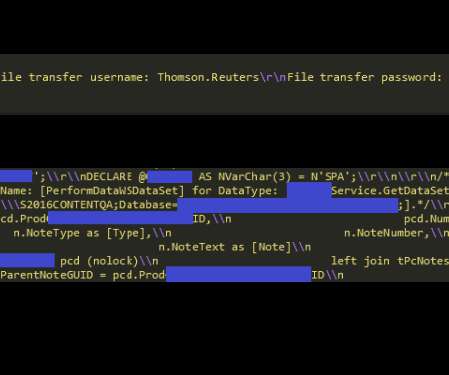
Security Affairs
OCTOBER 27, 2022
According to Mantas Sasnauskas, the Head of Security Research at Cybernews, this type of information would allow threat actors to gain an initial foothold in the systems used by companies working with Thomson Reuters. Either way, even if all of the data was essential, that doesn’t make it less sensitive if leaked. Why did it happen?

The Last Watchdog
AUGUST 14, 2019
Related: Lessons learned from Capital One breach Yet, I also had the chance to speak one-on-one with dozens of security vendors who are innovating like crazy to improve security. Companies have silos of security data that need the same type of visibility that EDR brings to the end point.

HL Chronicle of Data Protection
SEPTEMBER 27, 2018
states, have articulated distinct visions for how to address privacy concerns.” The RFC proposes seven desired outcomes that should underpin privacy protections: Transparency, control, reasonable minimization (of data collection, storage length, use, and sharing), security, access and correction, risk management, and accountability.

Data Protection Report
FEBRUARY 23, 2023
Processor obligations would include transparency (APP 1), Security (APP 11) and the Notifiable Data Breach scheme (NDB scheme) and, importantly, a contract would be required between the controller and processor governing the processing service.

The Texas Record
DECEMBER 16, 2019
Commvault’s data management software allows users to store and to manage their own data in the cloud while having access to customer support and to storage space that is able to keep up with the needs of the public sector. IP address, row and column data, geo-location, etc.).
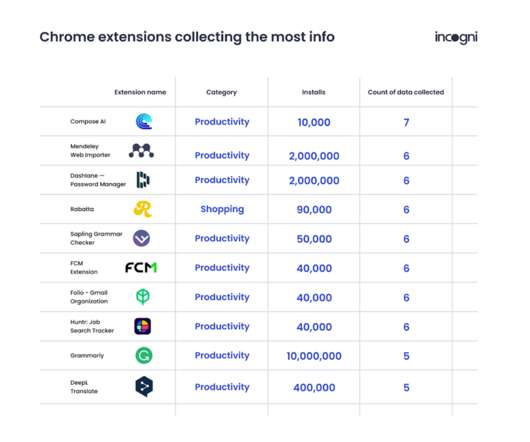
eSecurity Planet
NOVEMBER 29, 2022
Over 14 percent of the extensions studied by the researchers collect PII, more than 6 percent collect authentication data, 2.51 percent collect personal communications, and 1.21 percent collect financial and payment information. Chrome extensions used to aid in writing are the most data-hungry (79.5

IT Governance
JUNE 25, 2020
You could argue that these are exceptional circumstances and let the Regulation’s requirements slide, but that reasoning will look foolish as soon as the first pub suffers a cyber attack or data breach, and hundreds of customers’ personal data is exposed. All the latest cyber security news and advice .
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content