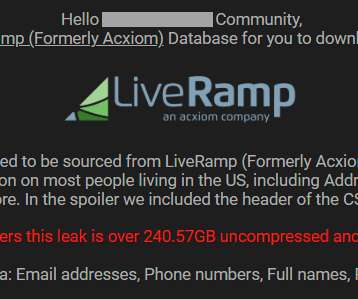
Meals on Wheels Disrupted by Suspected Ransomware Attack
IT Governance
JUNE 30, 2022
The disruption has caused major problems for the delivery of Meals on Wheels, a service that brings food to the elderly and vulnerable. Unfortunately, as our systems are not currently working, we will be unable to make many deliveries in the next few days. How did the cyber attack occur?































Let's personalize your content