NUVOLA: the new Cloud Security tool
Security Affairs
SEPTEMBER 28, 2022
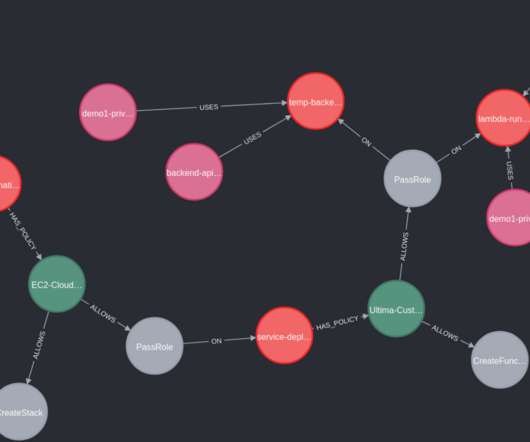
nuvola is the new open-source cloud security tool to address the privilege escalation in cloud environments. nuvola is the new open source security tool made by the Italian cyber security researcher Edoardo Rosa ( @_notdodo_ ), Security Engineer at Prima Assicurazioni. Cloud Security Context.















































Let's personalize your content