The latest variant of the RapperBot botnet adds cryptojacking capabilities
Security Affairs
MAY 14, 2023
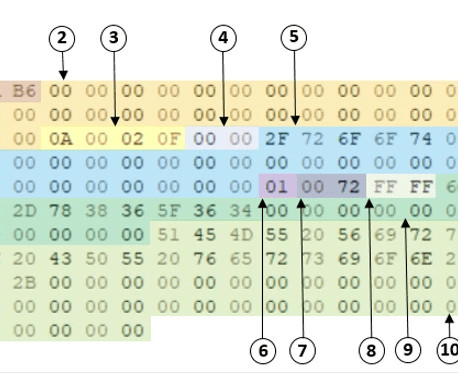
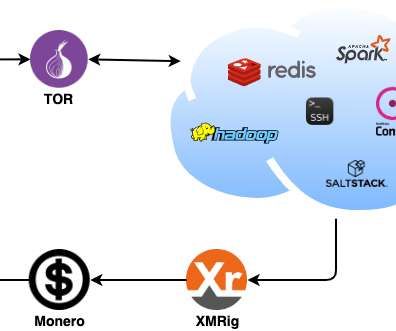
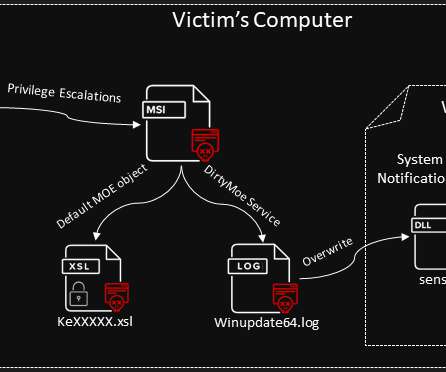
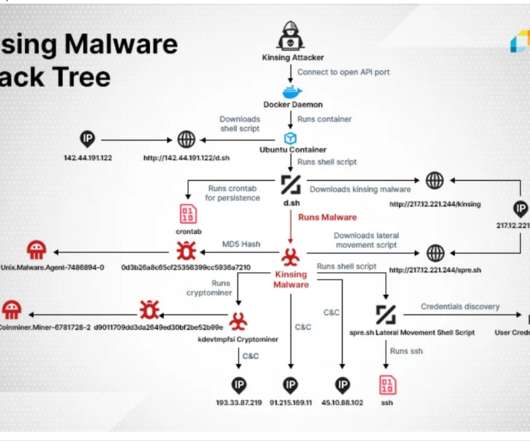
ssh/authorized_keys, anyone with the corresponding private key can authenticate the SSH server without supplying a password. Initially, they deployed and executed a separate Monero miner alongside the usual RapperBot binary, but starting from January 2023, they included the mining capabilities in the bot. ” continues the report.








































Let's personalize your content