Swiss real estate agency Neho fails to put a password on its systems
Security Affairs
MAY 31, 2023
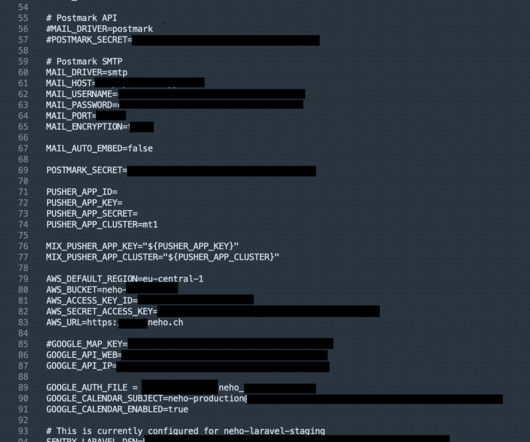
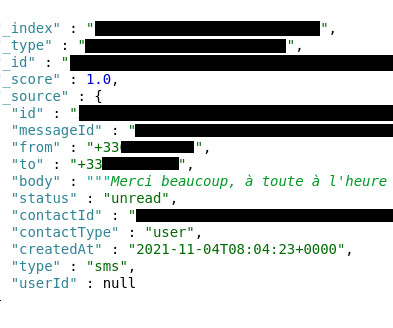
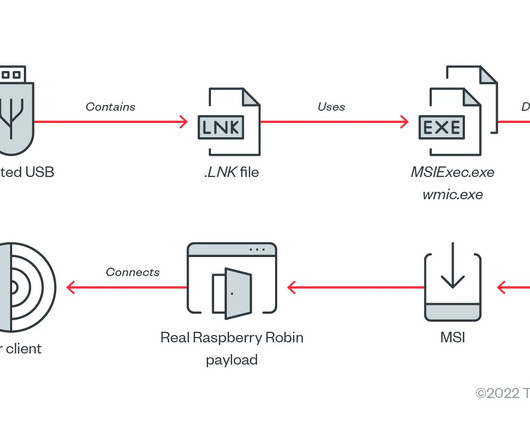
Using leaked data, threat actors could potentially breach the company’s internal systems and hijack official communication channels. The file contained PostgreSQL and Redis databases credentials, including host, port, username, and password. env) hosted on the official Neho’s website.










































Let's personalize your content