Law enforcement seized the Genesis Market cybercrime marketplace
Security Affairs
APRIL 5, 2023
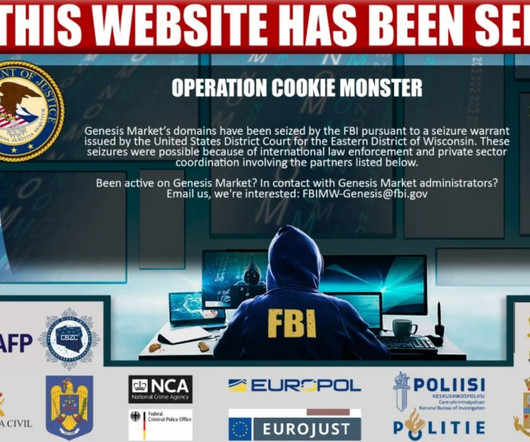
Law enforcement seized the Genesis Market black marketplace, a platform focused on the sale of stolen credentials, as part of Operation Cookie Monster. The FBI seized the Genesis Market , a black marketplace for stolen credentials that was launched in 2017.












































Let's personalize your content