REMnux Tools List for Malware Analysis
Lenny Zeltser
OCTOBER 13, 2020
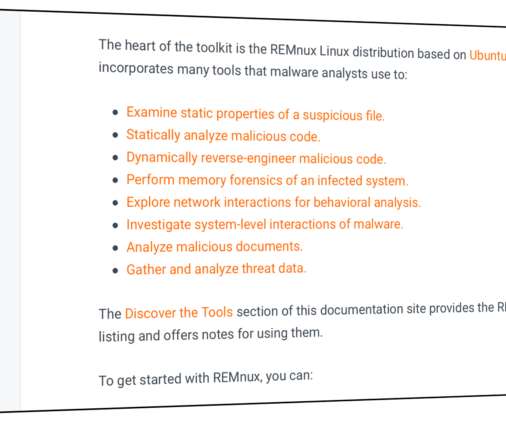
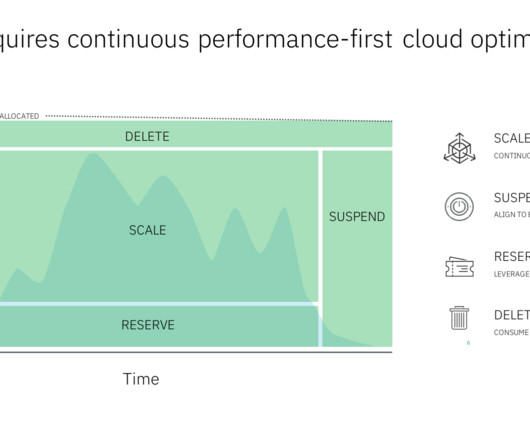
REMnux ® offers a curated collection of free tools for reverse-engineering or otherwise analyzing malicious software. To guide you through the process of examining malware, REMnux documentation lists the installed tools by category.















































Let's personalize your content