Data Breaches and Cyber Attacks in November 2023 – 519,111,354 Records Breached
IT Governance
DECEMBER 5, 2023
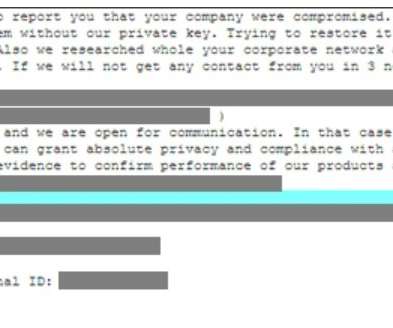
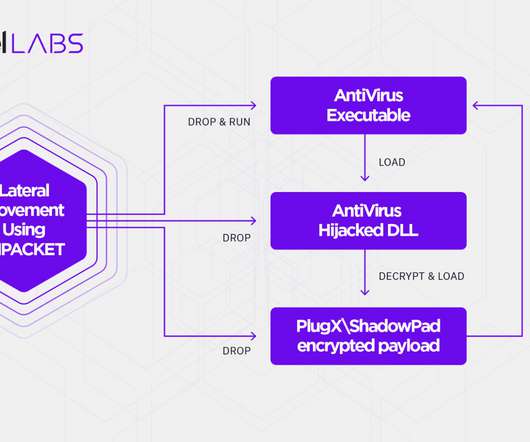
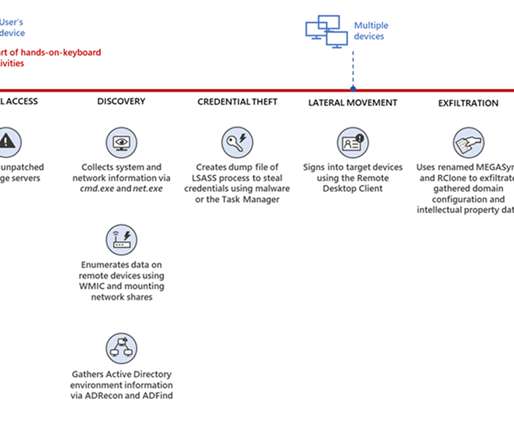
Data Breach Dashboard For a quick, one-page overview of this month’s findings, please use our Data Breach Dashboard: Note: From this month, zero-day vulnerabilities are excluded from the ‘unpatched or misconfigured’ category. This is part of the reason this category is lower than last month (24% vs 32%).
































Let's personalize your content