AI in commerce: Essential use cases for B2B and B2C
IBM Big Data Hub
MAY 17, 2024
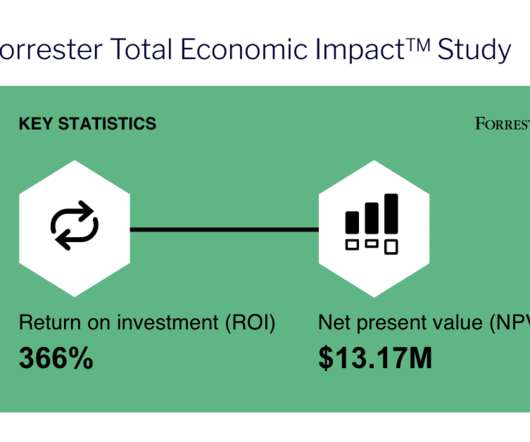
Key takeaways By implementing effective solutions for AI in commerce, brands can create seamless, personalized buying experiences that increase customer loyalty, customer engagement, retention and share of wallet across B2B and B2C channels. This includes trust in the data, the security, the brand and the people behind the AI.
















































Let's personalize your content