News alert: Massachusetts pumps $1.1 million into state college cybersecurity training programs
The Last Watchdog
OCTOBER 5, 2023
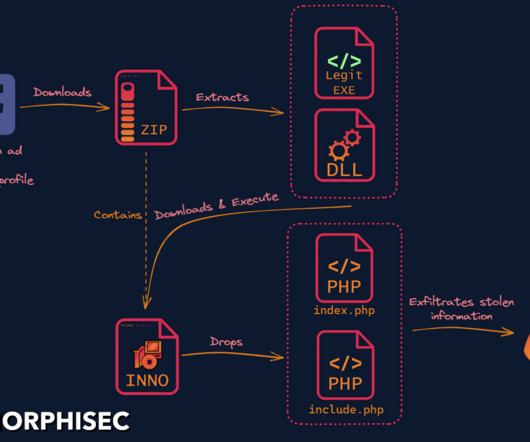
5, 2023 – Today, the Healey-Driscoll Administration kicked off Cybersecurity Month in Massachusetts with the announcement of $1,136,911 in funding to develop a new cybersecurity training center at MassBay Community College and support the existing center at Bridgewater State University. Worcester, Mass.,

















































Let's personalize your content