Using Event Notifications in your deployed solutions
IBM Big Data Hub
JUNE 21, 2023
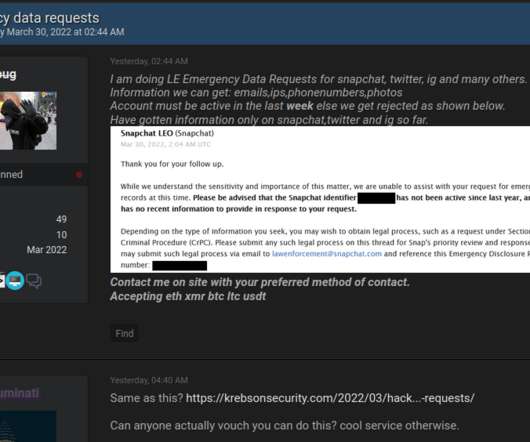
IBM Cloud Event Notifications is a service that can filter and route events received from other IBM Cloud services or custom applications to communication channels like email, SMS, push notifications, webhook, Slack, Microsoft® Teams, ServiceNow, IBM Cloud Code Engine and IBM Cloud Object Storage.















































Let's personalize your content