Authenticating Communication Screenshots
eDiscovery Daily
SEPTEMBER 13, 2021
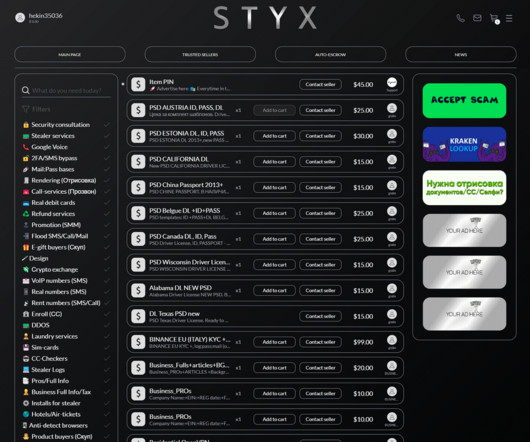
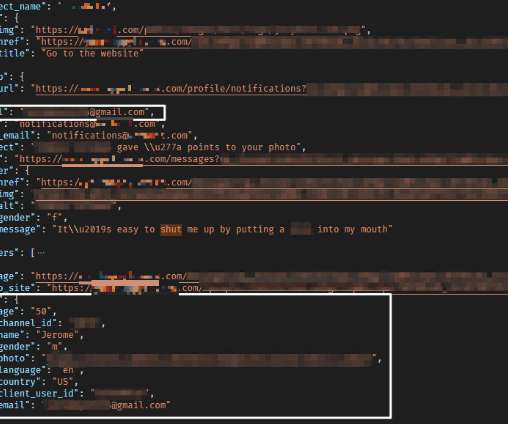
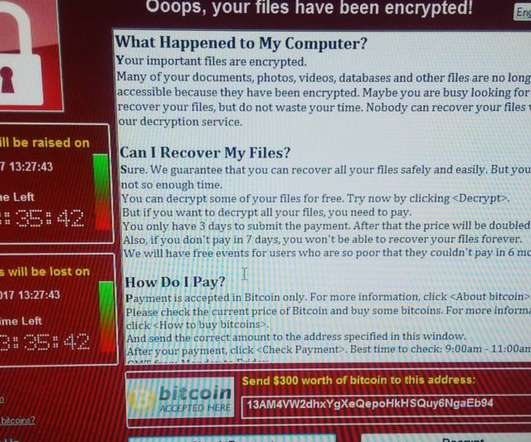
However, screenshots are not a reliable form of authenticating digital communication. The judge held that the anonymous source and the police couldn’t validate the authenticity of the evidence. [3]. How to Authenticate a Text Message Screenshot. How to Authenticate a Social Media Screenshot. Screenshot Failures in Court.














































Let's personalize your content