Next Generation Charting & Data Analysis
Enterprise Software Blog
JUNE 27, 2023
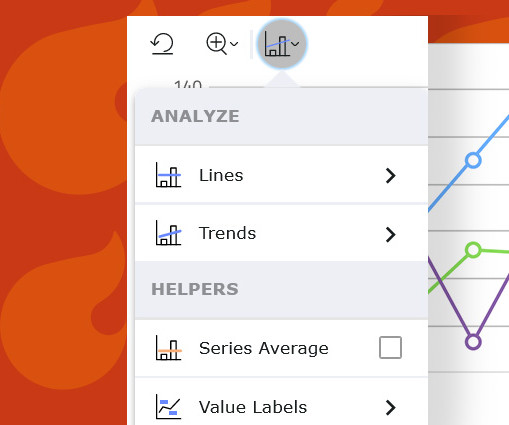
This allows you to simply select from a predefined set of properties on the chart to perform deeper data analysis on the data displayed in the chart. The Chart Toolbar includes Reset, Zoom and Analysis buttons at the top level. We are excited to ship this Preview with the most commonly requested analysis features.















































Let's personalize your content