Beginning Fuzz Cycle Automation: Improving Testing And Fuzz Development With Coverage Analysis
ForAllSecure
SEPTEMBER 25, 2019
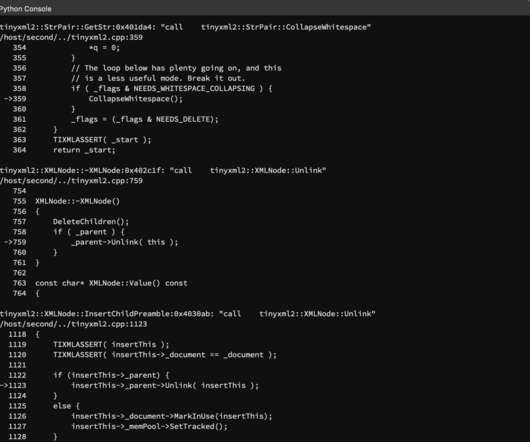
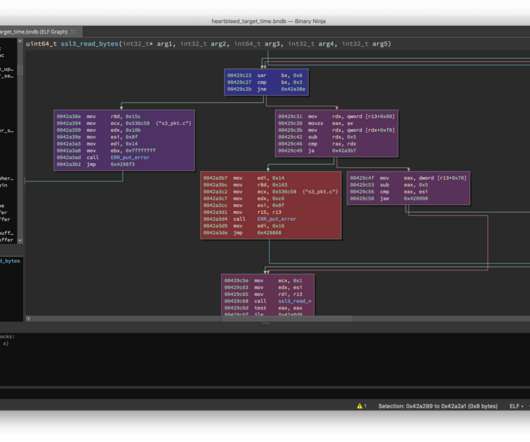
In my previous post , we covered using bncov to do open-ended coverage analysis tasks to inform our testing. This time we’ll take a look at how to write better tests in the form of harness programs (also known as fuzz drivers, programs written to exercise specific parts of the code) that we will use for fuzz testing.






























Let's personalize your content