New Linux variant of BIFROSE RAT uses deceptive domain strategies
Security Affairs
MARCH 3, 2024
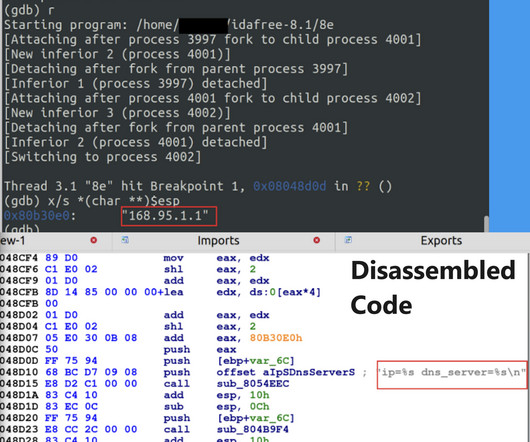
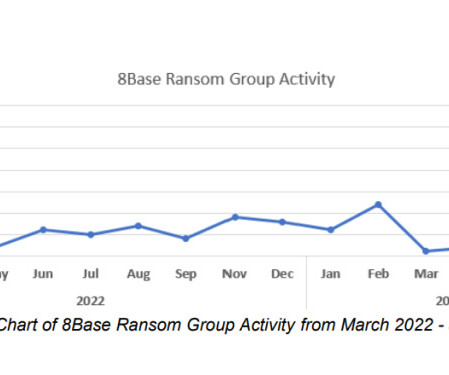
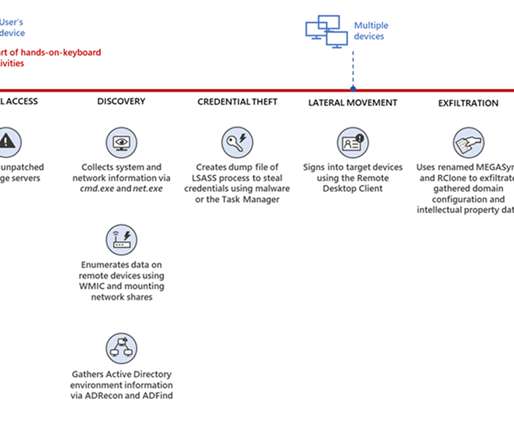
” reads the analysis published by Unit 42. By leveraging this deceptive domain, the threat actors behind Bifrost aim to bypass security measures, evade detection, and ultimately compromise targeted systems.” The recent sample of Linux variants of BIFROSE employes RC4 encryption to encrypt the collected victim data.











































Let's personalize your content