CDRThief Linux malware steals VoIP metadata from Linux softswitches
Security Affairs
SEPTEMBER 10, 2020
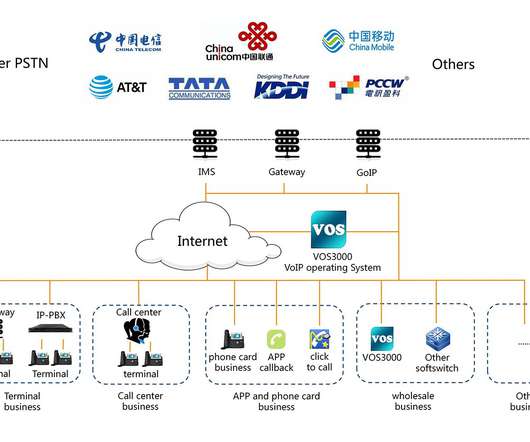
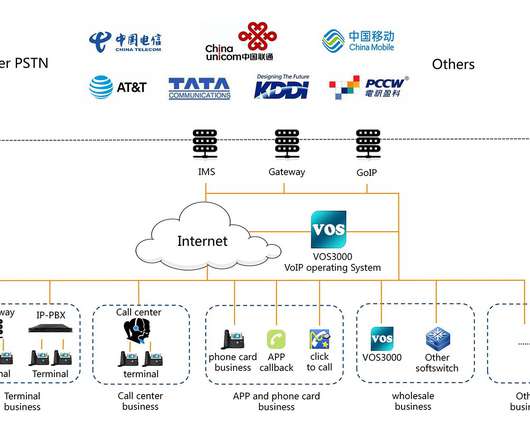
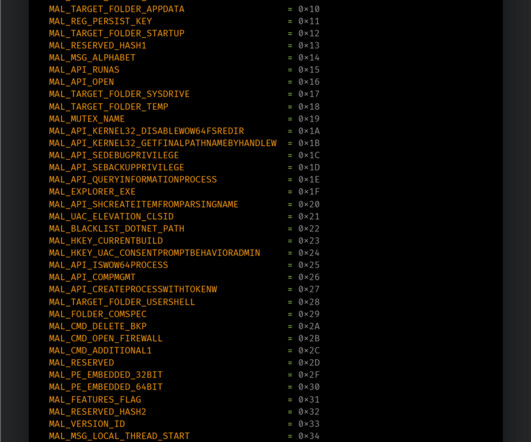
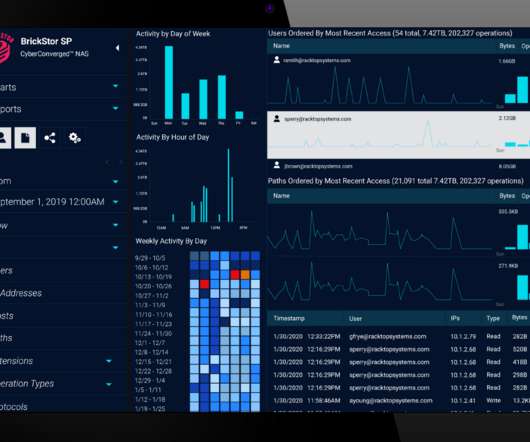
CDRThief specifically targets internal MySQL databases running in the devices to steal call metadata, including IP addresses of the callers, phone numbers, start time and duration of the call, call route, and call type. ” reads the analysis published by ESET. ” reads the analysis published by ESET.












































Let's personalize your content