ViperSoftX uses more sophisticated encryption and anti-analysis techniques
Security Affairs
APRIL 29, 2023
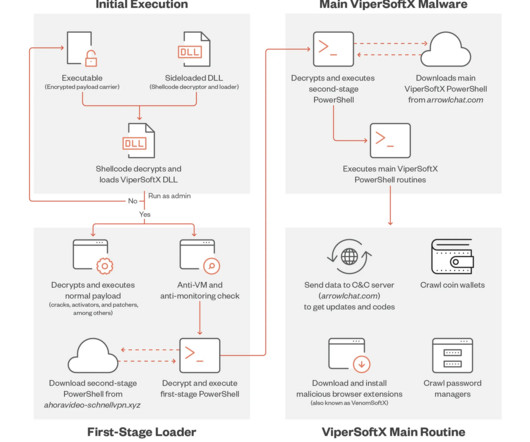
xyz pic.twitter.com/VLhISark8Y — Goldwave (@OGoldwave) March 13, 2023 The variant employed in the campaign supports a more sophisticated encryption method of byte remapping and a monthly rotation of the C2 server. ” reads the analysis published by Trend Micro. #ViperSoftX is back, doesn't look like much has changed.

































Let's personalize your content