Law Enforcement Access to Chat Data and Metadata
Schneier on Security
DECEMBER 10, 2021
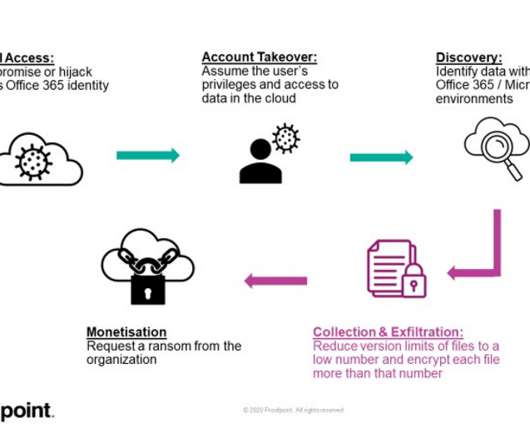
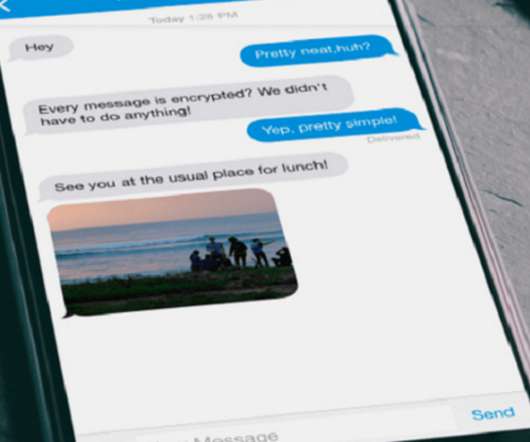
A January 2021 FBI document outlines what types of data and metadata can be lawfully obtained by the FBI from messaging apps. Lots of apps leak all sorts of metadata: iMessage and WhatsApp seem to be the worst. Signal protects the most metadata. Rolling Stone broke the story and it’s been written about elsewhere.











































Let's personalize your content