Doing Cloud Migration and Data Governance Right the First Time
erwin
OCTOBER 8, 2020
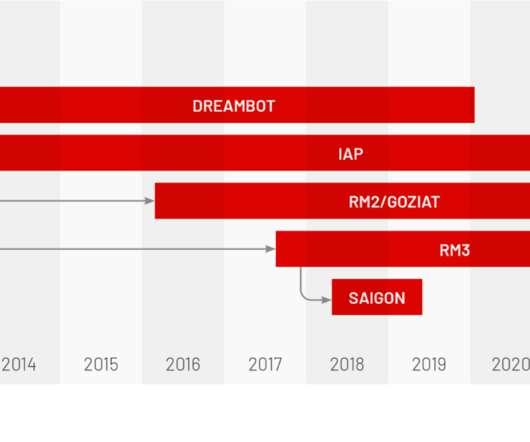
These tools range from enterprise service bus (ESB) products, data integration tools; extract, transform and load (ETL) tools, procedural code, application program interfaces (APIs), file transfer protocol (FTP) processes, and even business intelligence (BI) reports that further aggregate and transform data.











































Let's personalize your content