IT Governance Podcast 08.09.23: Electoral Commission (again), Meta, Pôle emploi
IT Governance
SEPTEMBER 7, 2023
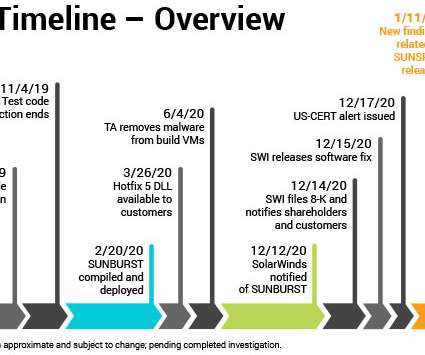
This week, we discuss security issues at the Electoral Commission, Meta’s appeal against daily GDPR fines, and a breach affecting 10 million users of the French unemployment agency Pôle emploi. Transcript: Hello and welcome to the IT Governance podcast for Friday, 8 September 2023.












































Let's personalize your content