Fulton County, Security Experts Call LockBit’s Bluff
Krebs on Security
FEBRUARY 29, 2024
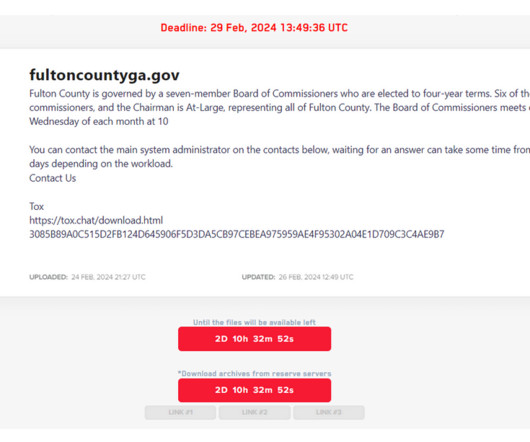
Security experts say LockBit was likely bluffing and probably lost most of the data when the gang’s servers were seized this month by U.S. “So the best thing for them to do would be to delete all other entries from their blog and stop defrauding honest people.” law enforcement. We have no control over that.







































Let's personalize your content