FBI Seizes Bot Shop ‘Genesis Market’ Amid Arrests Targeting Operators, Suppliers
Krebs on Security
APRIL 4, 2023
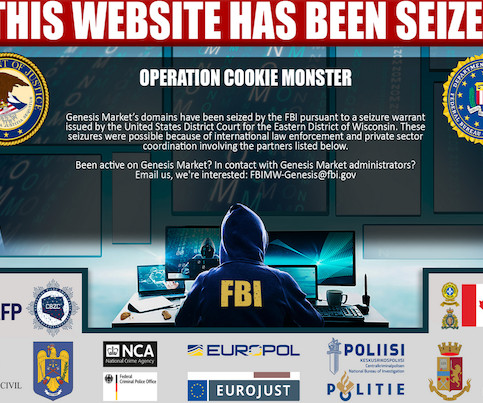
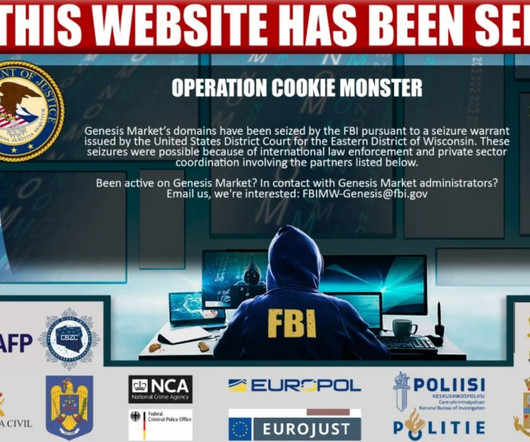
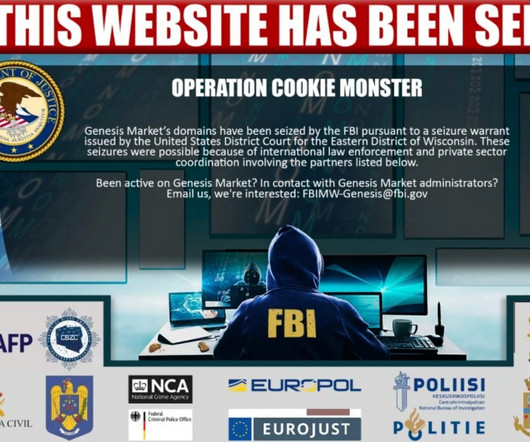
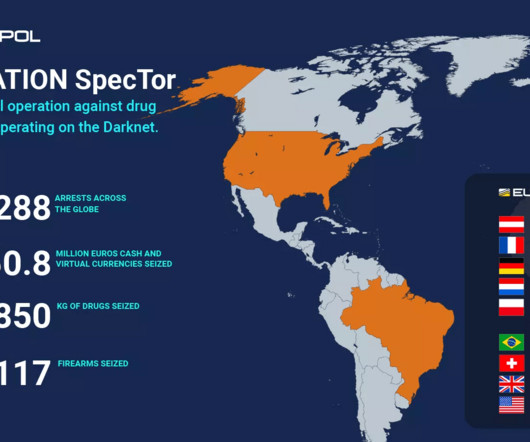
Several domain names tied to Genesis Market , a bustling cybercrime store that sold access to passwords and other data stolen from millions of computers infected with malicious software, were seized by the Federal Bureau of Investigation (FBI) today. ” a cybercrime forum ad for Genesis enthused.







































Let's personalize your content