Cisco Secure Access: SSE That Enables the Business
Data Breach Today
AUGUST 16, 2023
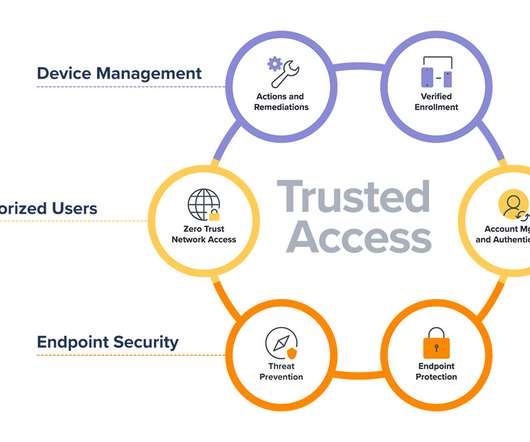
Cloud-Delivered Security Service Edge Solution Gives Efficient Hybrid Work Security Cisco Secure Access is a security service edge solution that delivers zero trust access to efficiently solve today's challenge of safely connecting anything to anywhere and reimagines the experience to make it better for users, easier for IT and safer for everyone.















































Let's personalize your content