Phish of GoDaddy Employee Jeopardized Escrow.com, Among Others
Krebs on Security
MARCH 31, 2020
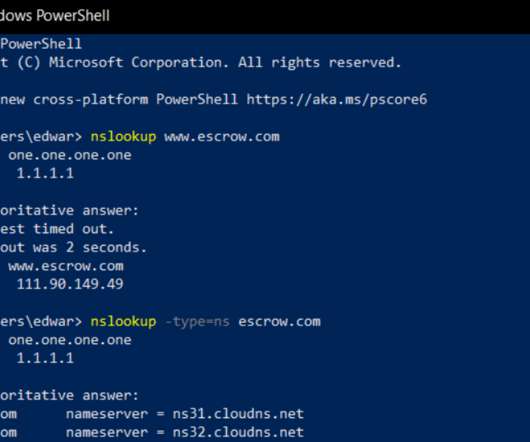
The incident gave the phisher the ability to view and modify key customer records, access that was used to change domain settings for a half-dozen GoDaddy customers, including transaction brokering site escrow.com. “This guy had access to the notes, and knew the number to call,” to make changes to the account, Barrie said.

































Let's personalize your content