Who Is the Network Access Broker ‘Babam’?
Krebs on Security
DECEMBER 3, 2021
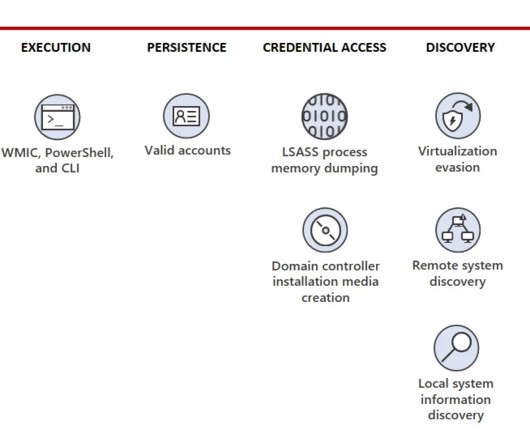
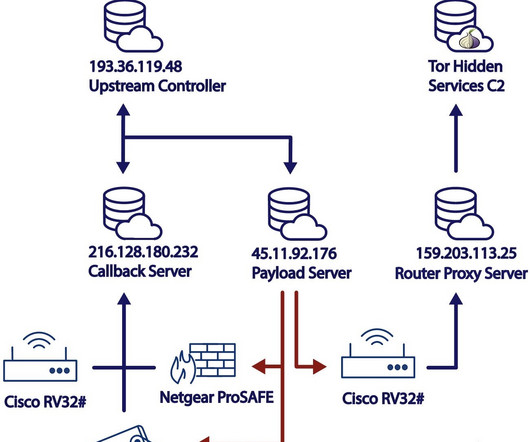
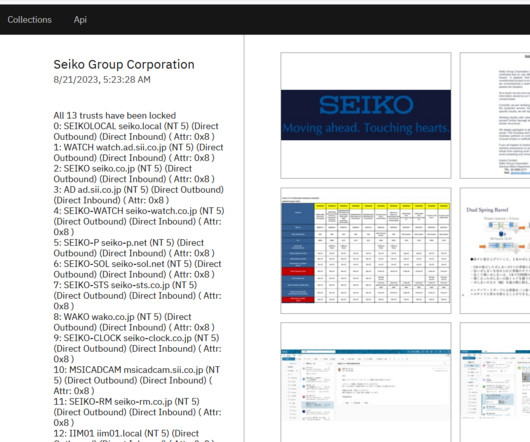
Rarely do cybercriminal gangs that deploy ransomware gain the initial access to the target themselves. More commonly, that access is purchased from a cybercriminal broker who specializes in acquiring remote access credentials — such as usernames and passwords needed to remotely connect to the target’s network.













































Let's personalize your content