List of Data Breaches and Cyber Attacks in 2023
IT Governance
JUNE 1, 2023
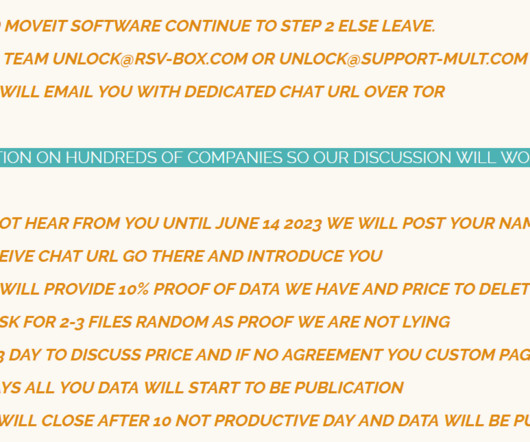
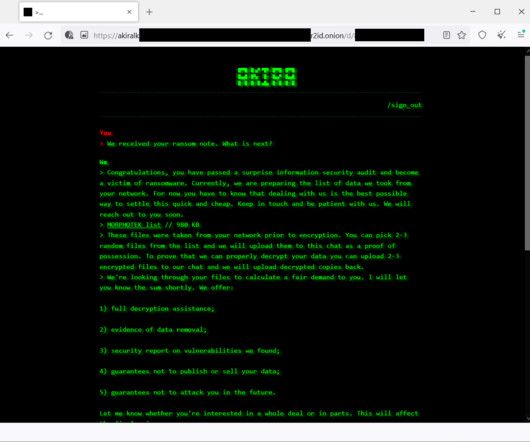
Welcome to our new-look list of data breaches and cyber attacks. So, each month, we’ll update this page with the latest figures and links, so be sure to bookmark it to keep an eye out for the latest data breach news. With that out of the way, it’s time to move on to May 2023. million unique email addresses and 2.6














































Let's personalize your content