Stayin’ Alive campaign targets high-profile Asian government and telecom entities. Is it linked to ToddyCat APT?
Security Affairs
OCTOBER 13, 2023
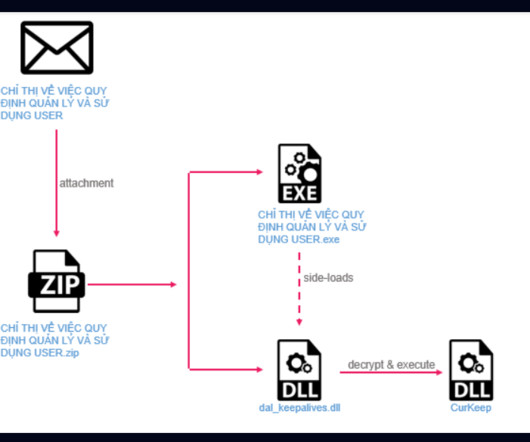
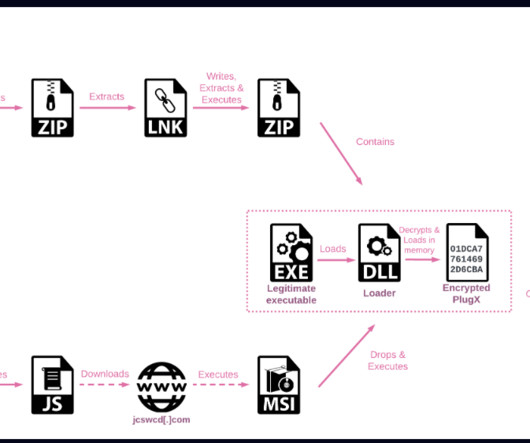
A cyberespionage campaign, tracked as Stayin’ Alive, targeted high-profile government and telecom entities in Asia. The APT group was discovered in June 2022 by Kaspersky which linked it to a series of attacks aimed at high-profile entities in Europe and Asia since at least December 2020. Is it linked to ToddyCat APT?









































Let's personalize your content